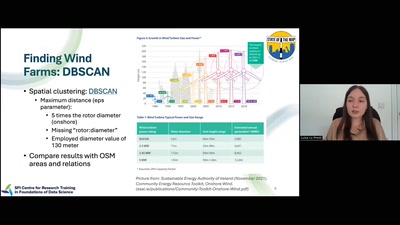
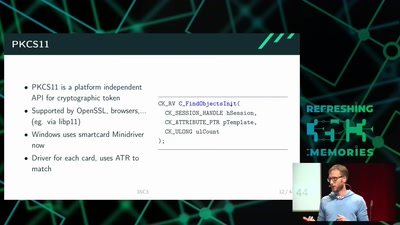
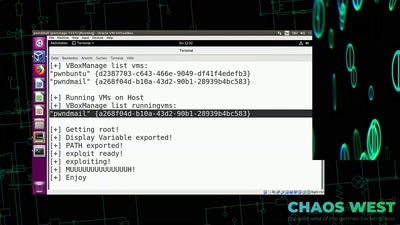
Search for "ar3itrary" returned 246 results

61 min
Computational Meta-Psychology
An Artificial Intelligence exploration into the creation of…

60 min
Attacking end-to-end email encryption
Efail, other attacks and lessons learned.
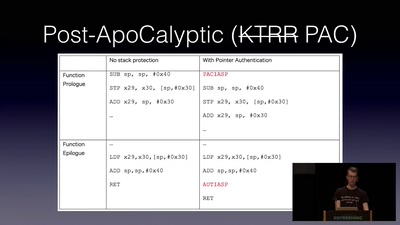
47 min
Jailbreaking iOS
From past to present

29 min
The Pirate Cinema
Creating mash-up movies by hidden activity and geography of…

58 min
Switches Get Stitches
Industrial System Ownership
60 min
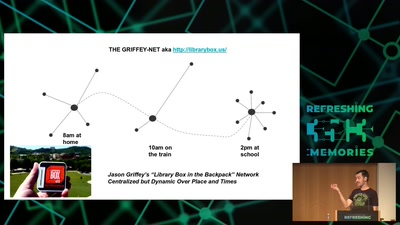
Wind: Off-Grid Services for Everyday People
Integrating nearby and offline connectivity with the…

46 min
SELECT code_execution FROM * USING SQLite;
--Gaining code execution using a malicious SQLite database

59 min
Memory Deduplication: The Curse that Keeps on Giving
A tale of 3 different memory deduplication based…

60 min
On the insecure nature of turbine control systems in power generation
A security study of turbine control systems in power…

54 min
Attacking Chrome IPC
Reliably finding bugs to escape the Chrome sandbox

61 min
Trustworthy secure modular operating system engineering
fun(ctional) operating system and security protocol…

64 min