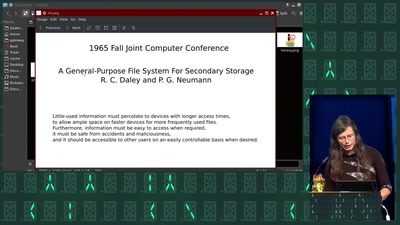
Search for "wose" returned 845 results
31 min
Working together in one place with Nextcloud
What's scaring Big Tech today

60 min
On the insecure nature of turbine control systems in power generation
A security study of turbine control systems in power…

61 min
ZFS - Universelles Dateisystem für Solaris, illumos, BSD, Windows... und Linux
Ein Streifzug durch die Welt der modernen Storage
58 min
Privacy & Stylometry
Practical Attacks Against Authorship Recognition Techniques

64 min
"Exploit" in theater
post-existentialism is the question, not post-privacy

59 min
Financial surveillance
Exposing the global banking watchlist

38 min
The impact of quantum computers in cybersecurity
Estimating the costs of algorithms for attacks and defense…

43 min