Search for "Ben" returned 8971 results
121 min
Lightning Talks - Day 4
where is my community?

25 min
Security Log Visualization with a Correlation Engine
What's inside your network?

58 min
Collapsing the European security architecture
More security-critical behaviour in Europe!
51 min
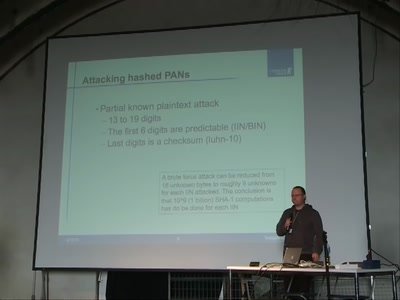
Strong encryption of credit card information
Attacks on common failures when encrypting credit card…
56 min
Hacking ideologies, part 2: Open Source, a capitalist movement
Free Software, Free Drugs and an ethics of death

53 min
The very early Computer Game History
How the games have become the first digital mass product
64 min
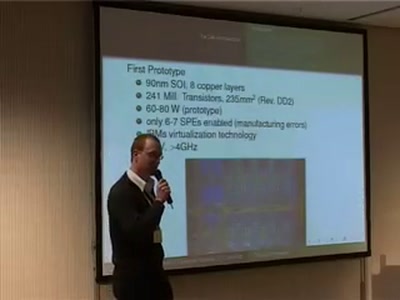
The Cell Processor
Computing of Tomorrow or Yesterday
56 min
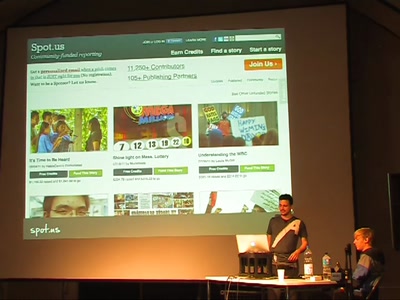
Rethinking online news
Journalism needs hackers to survive
57 min
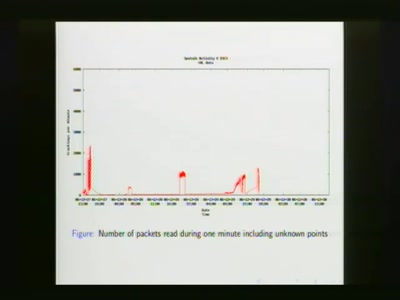
Analysis of Sputnik Data from 23C3
Attempts to regenerate lost sequences

57 min
Giving Great Workshops
You can create your own successful workshop
63 min
Exploiting Symbian
Symbian Exploit and Shellcode Development

53 min
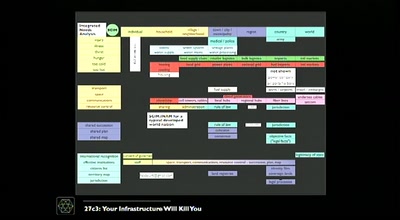
Towards a Single Secure European Cyberspace?
What the European Union wants. What the hackerdom can do..
60 min
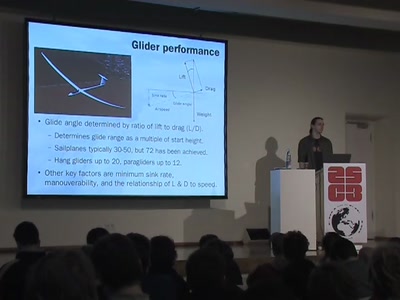
Flying for free
Exploiting the weather with unpowered aircraft
98 min
Hardware Hacking for Software Geeks
Essential Tips and Tricks
73 min
hacking smart phones
expanding the attack surface and then some

52 min
Personal experiences bringing technology and new media to disaster areas
Experiences from Iraq and post Katrina New Orleans
64 min
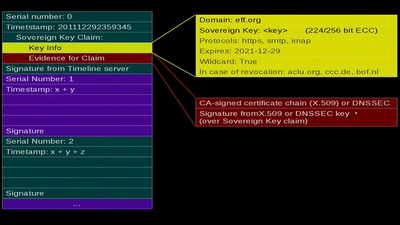
Sovereign Keys
A proposal for fixing attacks on CAs and DNSSEC

47 min
Small footprint inspection techniques for Android
Reverse engineering on Android platforms

61 min
SMS-o-Death
From analyzing to attacking mobile phones on a large scale.

63 min
Power gadgets with your own electricity
escape the basement and make the sun work for you

62 min