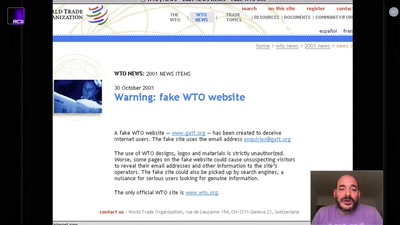
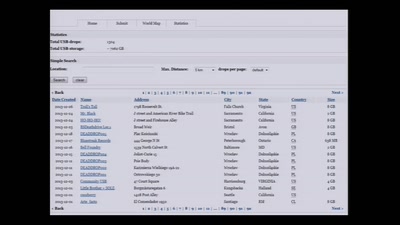
Search for "Shane" returned 1308 results

60 min
Ein Abgrund von Landesverrat
Wie es dazu kam und was daraus zu lernen ist

60 min
Sneaking In Network Security
Enforcing strong network segmentation, without anyone…

61 min
Untrusting the CPU
A proposal for secure computing in an age where we cannot…
57 min
Hello World!
How to make art after Snowden?

60 min
From Computation to Consciousness
How computation helps to explain mind, universe and…

57 min
TrustZone-M(eh): Breaking ARMv8-M's security
Hardware attacks on the latest generation of ARM Cortex-M…

62 min
Space Ops 101
An introduction to Spacecraft Operations
60 min
Software Defined Emissions
A hacker’s review of Dieselgate

46 min
CounterStrike
Lawful Interception

49 min
Electromagnetic Threats for Information Security
Ways to Chaos in Digital and Analogue Electronics

44 min
What the cyberoptimists got wrong - and what to do about it
Tech unexeptionalism and the monopolization of every…

55 min
ZombieLoad Attack
Leaking Your Recent Memory Operations on Intel CPUs

60 min
Open Source is Insufficient to Solve Trust Problems in Hardware
How Betrusted Aims to Close the Hardware TOCTOU Gap

60 min
The rise and fall of Internet voting in Norway
Evaluating a complex cryptographic implementation

57 min
Kryptographie nach Snowden
Was tun nach der mittelmäßigen Kryptographie-Apokalypse?

64 min
"Exploit" in theater
post-existentialism is the question, not post-privacy

54 min