Search for "csk" returned 1269 results
56 min
Deconstructing a Socialist Lawnmower
Obsolete Technologies + Critical Material Studies in Media…
50 min
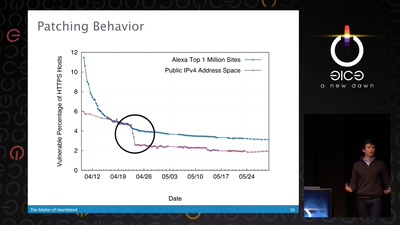
The Matter of Heartbleed
What went wrong, how the Internet reacted, what we can…

54 min
Kernel Tracing With eBPF
Unlocking God Mode on Linux
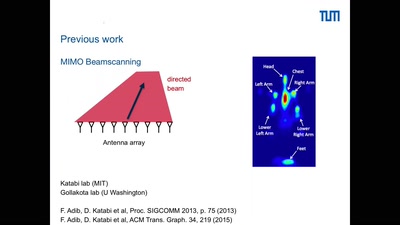
61 min
Holography of Wi-Fi radiation
Can we see the stray radiation of wireless devices? And…

62 min
Kyber and Post-Quantum Crypto
How does it work?

63 min
goto fail;
exploring two decades of transport layer insecurity

59 min
De-anonymizing Programmers
Large Scale Authorship Attribution from Executable Binaries…

63 min
Through a PRISM, Darkly
Everything we know about NSA spying
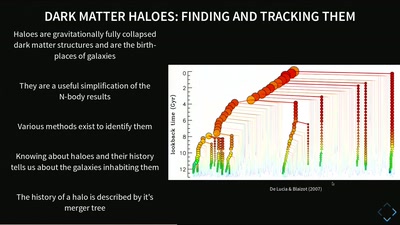
60 min
Simulating Universes
What Virtual Universes Can Tell Us About Our Own

60 min
The Only Thing We Know About Cyberspace Is That Its 640x480
One Terabyte of Kilobyte Age

58 min
Glitching For n00bs
A Journey to Coax Out Chips' Inner Secrets

59 min
Fernvale: An Open Hardware and Software Platform, Based on the (nominally) Closed-Source…
A Lawful Method for Converting Closed IP into Open IP

58 min
Schweiz: Netzpolitik zwischen Bodensee und Matterhorn
E-ID, E-Voting, Netzsperren und andere netzpolitische…

61 min