Search for "sven" returned 2148 results

40 min
What is this? A machine learning model for ants?
How to shrink deep learning models, and why you would want…

56 min
Viva la Vita Vida
Hacking the most secure handheld console

34 min
Little Services, Big Risks
Extending capability-based security models to achieve…
39 min
Transmission Control Protocol
TCP/IP basics

47 min
Bug class genocide
Applying science to eliminate 100% of buffer overflows
65 min
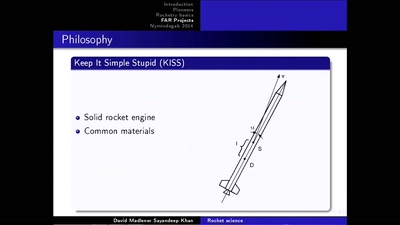
Rocket science – how hard can it be?
First steps into space with sounding rockets
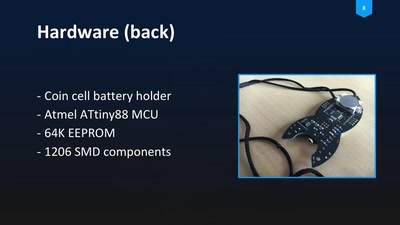
29 min
Blinkenrocket!
How to make a community project fly

63 min
The Case Against WikiLeaks: a direct threat to our community
How to understand this historic challenge and what we can…

61 min
Trustworthy secure modular operating system engineering
fun(ctional) operating system and security protocol…

39 min
Greenhouse Gas Emission Data
Public, difficult to access, and not always correct
62 min
Machine Dreams
Dreaming Machines

29 min
Pegasus internals
Technical Teardown of the Pegasus malware and Trident…

58 min
Paypals War on Terror
A Historical Re-Enactment of the PayPal14

56 min
Reality Check! Basel/Lagos?? In virtual reality?
An African tale of art, culture and technology

61 min
Now I sprinkle thee with crypto dust
Internet reengineering session

58 min