Search for "sec" returned 2717 results

40 min
An introduction to Firmware Analysis
Techniques - Tools - Tricks

36 min
Apple's iPhone 15: Under the C
Hardware hacking tooling for the new iPhone generation

40 min
What is this? A machine learning model for ants?
How to shrink deep learning models, and why you would want…

58 min
How to Break PDFs
Breaking PDF Encryption and PDF Signatures
36 min
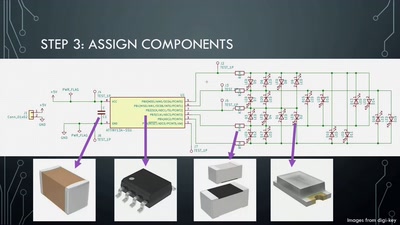
Artistic PCB Design and Fabrication
From doodle to manufacture: how I make mechanically…
59 min
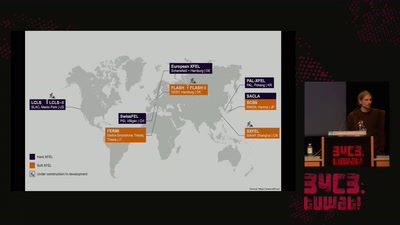
Free Electron Lasers
...or why we need 17 billion Volts to make a picture.

44 min
Lützerath Lebt! Einblicke in den Widerstand
Für globale Klimagerechtigkeit kämpfen
62 min
Internet, the Business Side
a try to explain the ecosystem
44 min
Why Nobody cares, and only You can save the World
Technology, Intuitions & Moral Expertise
63 min
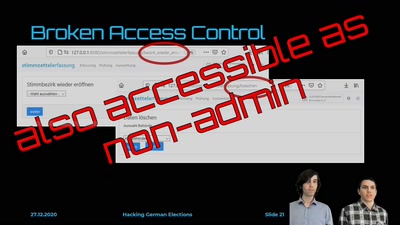
Hacking German Elections
Insecure Electronic Vote Counting - How It Returned and Why…

40 min