Search for "Leah" returned 1406 results

29 min
The Urban Organism
Hacking [in] Hong Kong

55 min
Inside Field Station Berlin Teufelsberg
The story of the NSA listening post – told by an ex-SIGINT…

26 min
Data Mining for Good
Using random sampling, entity resolution, communications…

41 min
Corona-Warn-App
Behind the scenes: Invisible, yet important

60 min
The rise and fall of Internet voting in Norway
Evaluating a complex cryptographic implementation

32 min
Finding the Weak Crypto Needle in a Byte Haystack
Automatic detection of key-reuse vulnerabilities

46 min
You can -j REJECT but you can not hide: Global scanning of the IPv6 Internet
Finding interesting targets in 128bit of entropy

63 min
Dissecting HDMI
Developing open, FPGA-based capture hardware for conference…

60 min
Check your privileges!
How to drop more of your privileges to reduce attack…
62 min
Machine Dreams
Dreaming Machines
44 min
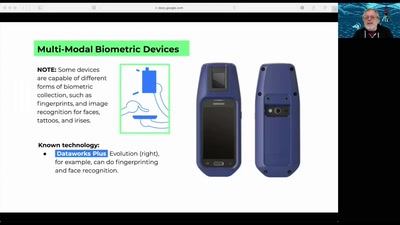
Spot the Surveillance
How to Identify Police Surveillance at Protests and Large…
41 min
Framing digital industry into planetary limits and transition policies
The environmental costs of digital industry and pathways to…

60 min