Search for "Sven" returned 2151 results
58 min
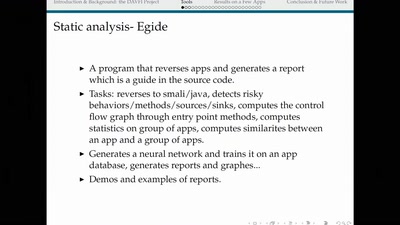
RFID Treehouse of Horror
Hacking City-Wide Access Control Systems
39 min
Decentralized energy production: green future or cybersecurity nightmare?
The cybersecurity dark side of solar energy when clouds are…

58 min
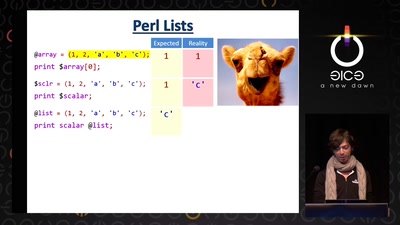
The Magic World of Searchable Symmetric Encryption
A brief introduction to search over encrypted data

61 min
DevOps but for artworks in museums
A look into pipelines ending in museums and not in the cloud

50 min
Internet censorship in the Catalan referendum
Overview of how the state censored and how it got…

58 min
07KINGSTON25 JAMAICA: MALARIA UPDATE Dispatches from Fort Meade
Reporting on the secret trial of Chelsea Manning
64 min
3 Years After Snowden: Is Germany fighting State Surveillance?
A Closer Look at the Political Reactions to Mass…

60 min
The Fight for Encryption in 2016
Crypto fight in the Wake of Apple v. FBI
56 min
Making Technology Inclusive Through Papercraft and Sound
Introducing the Love to Code Platform
47 min
Jailbreaking iOS
From past to present

61 min
Now I sprinkle thee with crypto dust
Internet reengineering session
39 min
Gamified Control?
China's Social Credit Systems
47 min
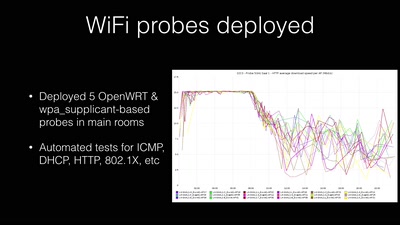
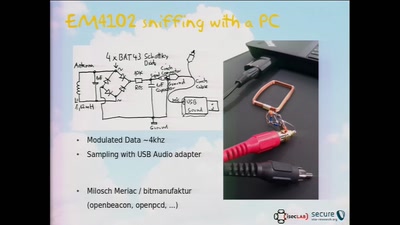
Finding Vulnerabilities in Internet-Connected Devices
A Beginner’s Guide

60 min
net neutrality: days of future past?
Taking stock after two years of net neutrality in the…

59 min