Search for "Ute Holl" returned 1413 results

59 min
Provable Security
How I learned to stop worrying and love the backdoor

59 min
We should share our secrets
Shamir secret sharing: How it works and how to implement it

47 min
Hardening hardware and choosing a #goodBIOS
Clean boot every boot - rejecting persistence of malicious…
61 min
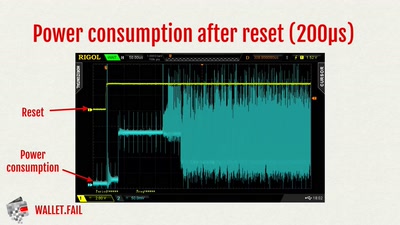
wallet.fail
Hacking the most popular cryptocurrency hardware wallets

51 min
Uncovering vulnerabilities in Hoermann BiSecur
An AES encrypted radio system
59 min
Towards General Purpose Reconfigurable Computing on Novena
FPGAs for Everybody with Novena

60 min
Shopshifting
The potential for payment system abuse

62 min
Calafou, postcapitalist ecoindustrial community
Building a space for grassroots sustainable technology…

61 min
Net Neutrality in Europe
alea iacta est
55 min
Cat & Mouse: Evading the Censors in 2018
Preserving access to the open Internet with circumvention…

58 min
Cyber all the Wassenaars
Export controls and exploit regulations: braindead and…

51 min
Funky File Formats
Advanced binary tricks

62 min
Corporate surveillance, digital tracking, big data & privacy
How thousands of companies are profiling, categorizing,…
72 min
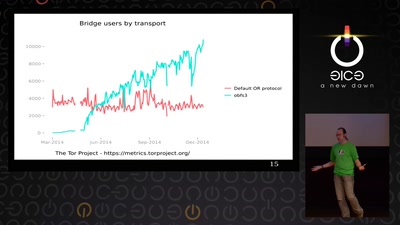
State of the Onion
Neuland

55 min
The Gospel of IRMA
Attribute Based Credentials in Practice

59 min
Memory Deduplication: The Curse that Keeps on Giving
A tale of 3 different memory deduplication based…

63 min
Don't stop 'til you feel it
Artistic interventions in climate change

58 min
How risky is the software you use?
CITL: Quantitative, Comparable Software Risk Reporting

54 min