Search for "Jon" returned 9471 results

38 min
What your phone won’t tell you
Uncovering fake base stations on iOS devices

30 min
All Our Shared Spectrum Are Belong to Us
Visualizing WLAN Channel Usage on OpenWRT

57 min
To Make Hearts Bleed
A Native Developer's Account On SSL

42 min
Just in Time compilers - breaking a VM
Practical VM exploiting based on CACAO
46 min
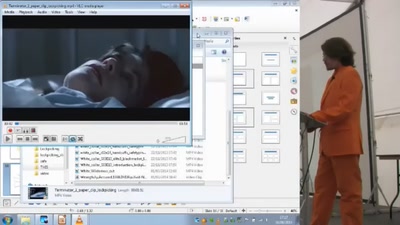
Bugged Files
Is Your Document Telling on You?

83 min
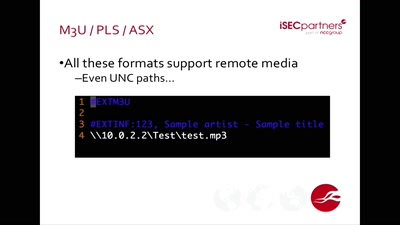
rechtsbelehrung.com
Recht autonom - Geschäftsfähigkeit und Haftung von KIs,…
47 min
The Past in the Cloud
Wie man auch morgen noch die Software von gestern hacken…
83 min
SDR - Fluch, Segen, Möglichkeiten
Der Einsatz von SDR-Technik aus Sicht des Technikers,…
40 min
No roborders, no nation, or: smile for a European surveillance propagation
How an agency implements Fortress Europe by degrading…
56 min
The importance of resisting Excessive Government Surveillance
Join me in exposing and challenging the constant violations…

45 min
Homegrown Interactive Tables
Any Technology Sufficiently Advanced is Indistinguishable…

56 min
eMMC hacking, or: how I fixed long-dead Galaxy S3 phones
A journey on how to fix broken proprietary hardware by…
98 min
Towards automatic end to end mail encryption
mail encryption overview and hands-on Autocrypt sessions

43 min
Pirate Radio
Running a Station and Staying on the Air

38 min
People, Profiles and Trust
On interpersonal trust in web-mediated social spaces

32 min
Technology and Mass Atrocity Prevention
Overview on Current Efforts - We Need Moar H4x0rs?!

61 min
Correcting copywrongs
European copyright reform is finally on the horizon

90 min
WSIS - An Overview
The World Summit on the Information Society Revisited

60 min
Let's talk about Desktop Linux Platform Issues
What's holding back Linux on the desktop?

45 min
Machine-to-machine (M2M) security
When physical security depends on IT security
54 min
Contemporary Profiling of Web Users
On Using Anonymizers and Still Get Fucked

46 min
Signal Intelligence und Electronic Warfare
Wie man nach Hause telefoniert, ohne von einer Rakete…

47 min