Search for "Ute Holl" returned 1413 results

63 min
The Global Assassination Grid
The Infrastructure and People behind Drone Killings

63 min
Don't stop 'til you feel it
Artistic interventions in climate change
40 min
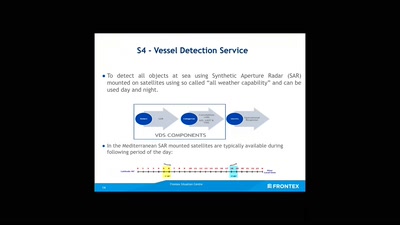
No roborders, no nation, or: smile for a European surveillance propagation
How an agency implements Fortress Europe by degrading…

54 min
AMD x86 SMU firmware analysis
Do you care about Matroshka processors?
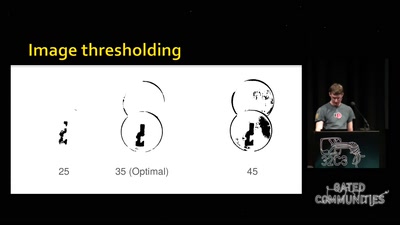
44 min
Replication Prohibited
3D printed key attacks
42 min
Union Busting
What is it and why you should care

58 min
Wie klimafreundlich ist Software?
Einblicke in die Forschung und Ausblick in die…

55 min
ZombieLoad Attack
Leaking Your Recent Memory Operations on Intel CPUs

63 min
goto fail;
exploring two decades of transport layer insecurity

64 min
Technical aspects of the surveillance in and around the Ecuadorian embassy in London
Details about the man hunt for Julian Assange and Wikileaks

46 min
SELECT code_execution FROM * USING SQLite;
--Gaining code execution using a malicious SQLite database
58 min
Script Your Car!
Using existing hardware platforms to integrate python into…
58 min
Confessions of a future terrorist
A rough guide to over-regulating free speech with…

60 min
Lets break modern binary code obfuscation
A semantics based approach

32 min
Finding the Weak Crypto Needle in a Byte Haystack
Automatic detection of key-reuse vulnerabilities

59 min
Visiting The Bear Den
A Journey in the Land of (Cyber-)Espionage

61 min
Trustworthy secure modular operating system engineering
fun(ctional) operating system and security protocol…

59 min