Search for "Ben" returned 8980 results

62 min
Security and anonymity vulnerabilities in Tor
Past, present, and future

50 min
Data Analysis in Terabit Ethernet Traffic
Solutions for monitoring and lawful interception within a…

87 min
Tor and China
Design of a blocking-resistant anonymity system

47 min
Fun with NFC Mobile Phones
Near Field Communication

42 min
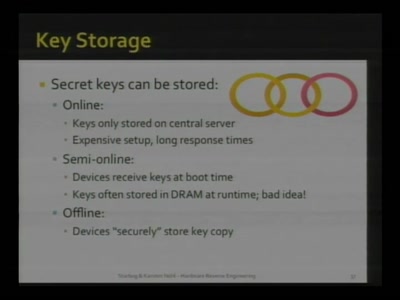
From Ring Zero to UID Zero
A couple of stories about kernel exploiting
61 min
Time is on my Side
Exploiting Timing Side Channel Vulnerabilities on the Web

53 min
Blackberry: call to arms, some provided
Teach yourself upper management in 22 days

43 min
Fudging with Firmware
Firmware reverse-engineering tactics

56 min
Rootkits in your Web application
Achieving a permanent stealthy compromise of user accounts…

47 min
WIPO Broadcasting Treaty
Lobbying on an International Scale
50 min
FAIFA: A first open source PLC tool
PowerLineCommunications has now their open source tool

45 min
Secure Network Server Programming on Unix
Techniques and best practices to securely code your network…

59 min
Understanding buffer overflow exploitation
The fascinating interplay of CPU, stack, C-compiler and…

48 min
The Privacy Workshop Project
Enhancing the value of privacy in todays students view
62 min
Cellular protocol stacks for Internet
GPRS, EDGE, UMTS, HSPA demystified

60 min