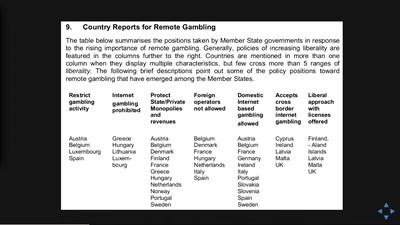
Search for "sven" returned 2148 results

65 min
The Untold Story of Edward Snowden’s Escape from Hong Kong
and How You Can Help the Refugees Who Saved His Life

53 min
Surveilling the surveillers
About military RF communication surveillance and other…

103 min
Comparison of WAN IGP protocols
RSTP+flooding/learning for Ethernet, OSPFv2 for IPv4, and…

62 min
The Internet (Doesn't) Need Another Security Guide
Creating Internet Privacy and Security Resources That Don't…
58 min
Hacking how we see
A way to fix lazy eye?
59 min
The Ultimate SPC700 Talk
The hardware behind the music of Super Mario World, Chrono…
41 min
Conquering Large Numbers at the LHC
From 1 000 000 000 000 000 to 10: Breaking down 14 Orders…

33 min
Turing Complete User
What can be done to protect the term, the notion and the…

46 min
Sendezentrum: Who Killed The Internet?
And a promising alternative for Public Communication and…

39 min
Recharge your batteries with us
– an empowering journey through the energy transition
42 min
Measuring radioactivity using low-cost silicon sensors
A DIY particle physics detector in a tin box.
43 min
The Mars Rover On-board Computer
How Curiosity's Onboard Computer works, and what you can…

44 min