Search for "xif" returned 1978 results
36 min
Understanding the Snooper’s Charter
Theresa May’s effort to abolish privacy

61 min
Now I sprinkle thee with crypto dust
Internet reengineering session

57 min
Protecting the Wild
Conservation Genomics between Taxonomy, Big Data,…

29 min
Infocalypse now: P0wning stuff is not enough
Several failure modes of the hacker scene
27 min
Maritime Robotics
Hackers, I call thee to our Oceans!

53 min
Surveilling the surveillers
About military RF communication surveillance and other…

47 min
Hardening hardware and choosing a #goodBIOS
Clean boot every boot - rejecting persistence of malicious…
50 min
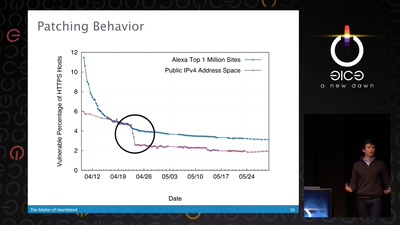
The Matter of Heartbleed
What went wrong, how the Internet reacted, what we can…
41 min
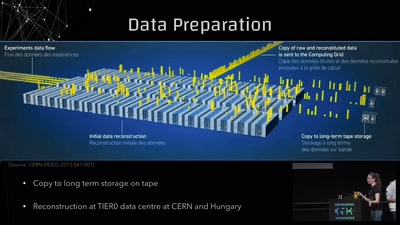
Conquering Large Numbers at the LHC
From 1 000 000 000 000 000 to 10: Breaking down 14 Orders…

29 min
The Pirate Cinema
Creating mash-up movies by hidden activity and geography of…

69 min
cryptocurrencies, smart contracts, etc.: revolutionary tech?
short answer: Yes!
39 min
Transmission Control Protocol
TCP/IP basics

61 min
The architecture of a street level panopticon
How drones, IMSI Catchers, and cameras are shaping our…

64 min
It Always Feels Like the Five Eyes Are Watching You
Five Eyes’ Quest For Security Has Given Us Widespread…
36 min
Wheel of Fortune
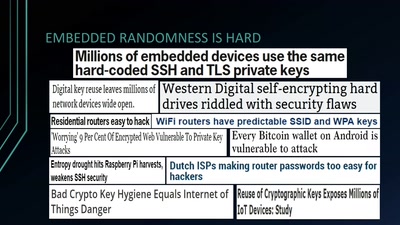
Analyzing Embedded OS Random Number Generators
39 min
Gamified Control?
China's Social Credit Systems

33 min







