Search for "Ben" returned 8981 results

60 min
Data Retention and PNR
The Brussels Workshop
45 min
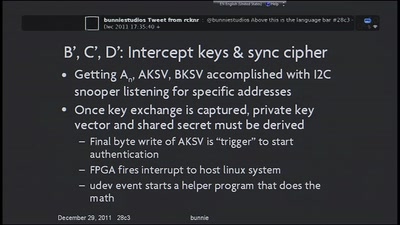
Implementation of MITM Attack on HDCP-Secured Links
A non-copyright circumventing application of the HDCP…

59 min
10GE monitoring live!
How to find that special one out of millions

65 min
Body hacking
Functional body modification

92 min
Security Nightmares 2009 (English interpretation)
Or: about what we will laugh next year

163 min
Lightning Talks 3
5 Minutes of Fame

63 min
<NO>OOXML - A 12 euros campaign
Against Microsoft Office's broken standard

52 min
Adventures in Mapping Afghanistan Elections
The story of 3 Ushahidi mapping and reporting projects.

26 min
Data Mining the Israeli Census
Insights into a publicly available registry
44 min
Unusual Web Bugs
A Web Hacker's Bag O' Tricks

68 min
"Spoilers, Reverse Green, DECEL!" or "What's it doing now?"
Thoughts on the Automation and its Human interfaces on…

33 min
Enabling Innovation in Europe
Hacker Spaces, Startups, and a new approach to social…
58 min
Hacking the iPhone
Pwning Apple's Mobile Internet Device

113 min
"Xbox" and "Xbox 360" Hacking
17 Mistakes Microsoft Made in the Xbox Security System &…

72 min
Lightning Talks - Day 3
where is my community?
46 min
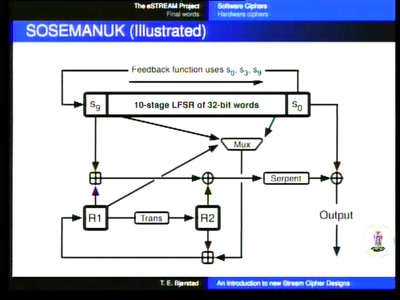
An introduction to new stream cipher designs
Turning data into line noise and back
53 min
Crouching Powerpoint, Hidden Trojan
An analysis of targeted attacks from 2005 to 2007
56 min
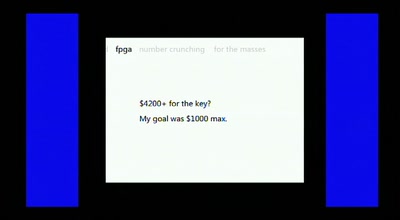
Distributed FPGA Number Crunching For The Masses
How we obtained the equivalent power of a Deep Crack for a…
76 min
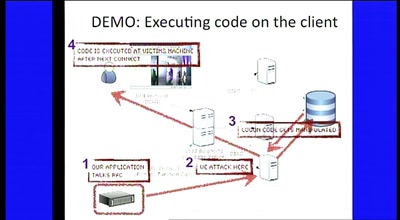
Rootkits and Trojans on Your SAP Landscape
SAP Security and the Enterprise

42 min
Inside the Mac OS X Kernel
Debunking Mac OS Myths

58 min
The Infinite Library
Storage and Access of Pornographic Information

125 min


