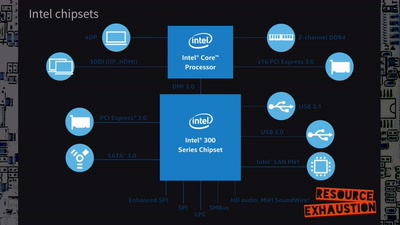
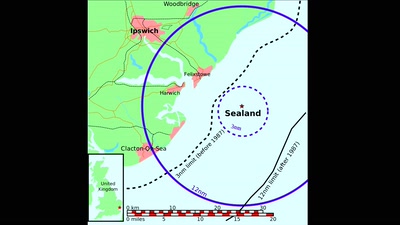
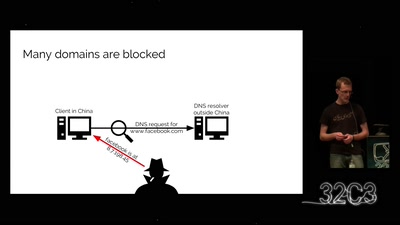
Search for "Sven" returned 2036 results

30 min
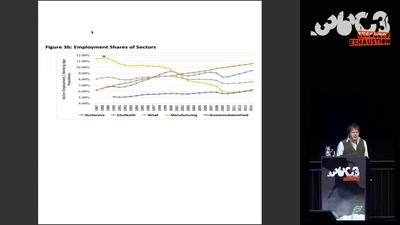
Privacy and Consumer Markets
Reversing the Surveillance Business Model

56 min
Household, Totalitarianism and Cyberspace
Philosophical Perspectives on Privacy Drawing on the…
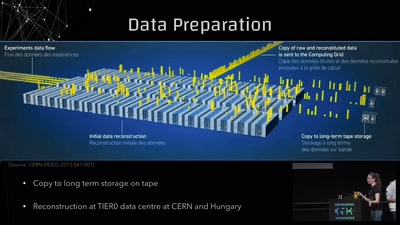
41 min
Conquering Large Numbers at the LHC
From 1 000 000 000 000 000 to 10: Breaking down 14 Orders…
31 min
Growing Up Software Development
From Hacker Culture to the Software of the Future

32 min
Why Do We Anthropomorphize Computers?...
...and dehumanize ourselves in the process?
60 min
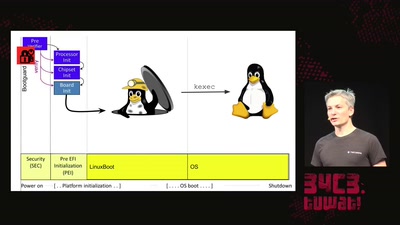
Opening Closed Systems with GlitchKit
'Liberating' Firmware from Closed Devices with Open Source…
60 min
Desperately Seeking Susy
A farewell to a bold proposal?
45 min
SearchWing
Open source drones for Search & Rescue

48 min
Don't Ruck Us Too Hard - Owning Ruckus AP Devices
3 different RCE vulnerabilities on Ruckus Wireless access…
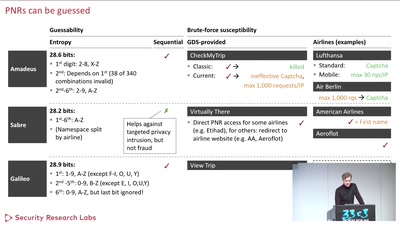
59 min
Where in the World Is Carmen Sandiego?
Becoming a secret travel agent
60 min