Search for "olf" returned 7379 results
65 min
PicoLisp Application Development
Interactive development of PicoLisp database applications

64 min
Source Code and Cross-Domain Authorship Attribution
The Role of Stylometry in Privacy

56 min
Console Hacking 2008: Wii Fail
Is implementation the enemy of design?
40 min
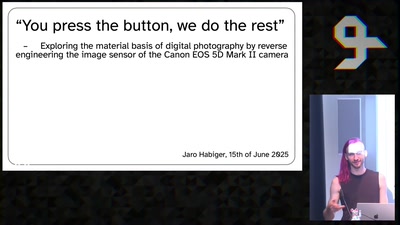
“You press the button, we do the rest”
Exploring the material basis of digital photography by…

30 min
Syrian Archive
Preserving documentation of human rights violations

55 min
Our daily job: hacking the law
The key elements of policy hacking

61 min
CAESAR and NORX
Developing the Future of Authenticated Encryption

52 min
WiFi Long Shots
Wireless connections of 20km and more

58 min
The Infinite Library
Storage and Access of Pornographic Information
31 min
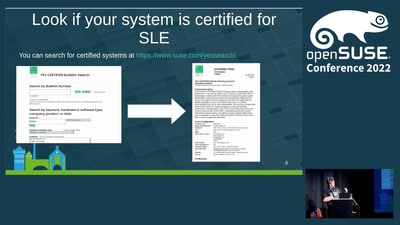
Will my hardware work with openSUSE?
Don't be afraid of the kernel
46 min