Search for "Apex" returned 174 results

57 min
TrustZone-M(eh): Breaking ARMv8-M's security
Hardware attacks on the latest generation of ARM Cortex-M…

55 min
Der PC-Wahl-Hack
Analyse einer Wahlsoftware
56 min
Running your own 3G/3.5G network
OpenBSC reloaded

41 min
Why Railway Is Safe But Not Secure
Security Of Railway Communication Protocols

63 min
Reconstructing narratives
transparency in the service of justice

61 min
QualityLand
Lesung

45 min
Triggering Deep Vulnerabilities Using Symbolic Execution
Deep program analysis without the headache
61 min
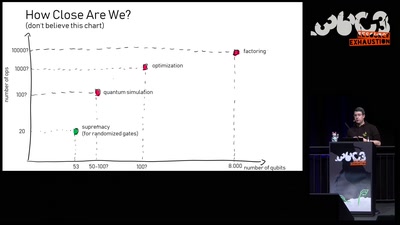
Quantum Computing: Are we there yet?
An introduction to quantum computing and a review of the…

55 min
What is Good Technology?
Answers & practical guidelines for engineers.

50 min
Internet censorship in the Catalan referendum
Overview of how the state censored and how it got…

58 min
Decoding Contactless (Card) Payments
An Exploration of NFC Transactions and Explanation How…

55 min
White-Box Cryptography
Survey

59 min
Visiting The Bear Den
A Journey in the Land of (Cyber-)Espionage

64 min
Cory Doctorow – Fireside Chat
Reading and Q&A

57 min