Search for "Erik" returned 194 results

60 min
Lockpicking in the IoT
...or why adding BTLE to a device sometimes isn't smart at…

60 min
My Robot Will Crush You With Its Soft Delicate Hands!
How to design and fabricate soft robots using everyday…

32 min
Finding the Weak Crypto Needle in a Byte Haystack
Automatic detection of key-reuse vulnerabilities

36 min
A Blockchain Picture Book
Blockchain origins and related buzzwords, described in…

40 min
Verlorene Domains, offene Türen
Was alte Behördendomains verraten
64 min
Hacking the Media: Geflüchtete schmuggeln, Nazis torten, Pässe fälschen
Warum wir zivilen Ungehorsam und Subversion mehr brauchen…

31 min
A Tale of Two Leaks:
How Hackers Breached the Great Firewall of China

54 min
Tactical Embodiment
Activism and Performance In Hostile Spaces Online

44 min
Exploiting PHP7 unserialize
teaching a new dog old tricks

46 min
SELECT code_execution FROM * USING SQLite;
--Gaining code execution using a malicious SQLite database

32 min
Why Do We Anthropomorphize Computers?...
...and dehumanize ourselves in the process?
42 min
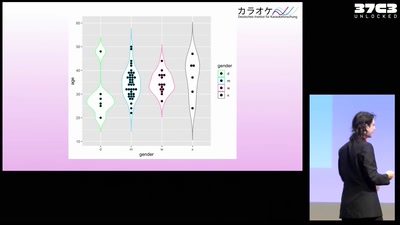
37C3 カラオケ – Herausforderungen der aktuellen Karaokeforschung
vom Deutschen Institut für Karaokeforschung

44 min