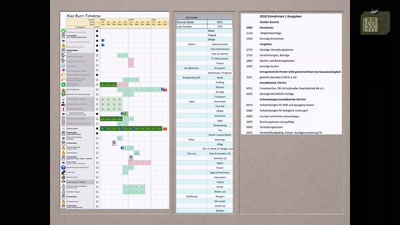
Search for "Hoang" returned 154 results

61 min
Copywrongs 2.0
We must prevent EU copyright reform from breaking the…

60 min
APT Reports and OPSEC Evolution, or: These are not the APT reports you are looking for
How advanced threat actors learn and change with innovation…
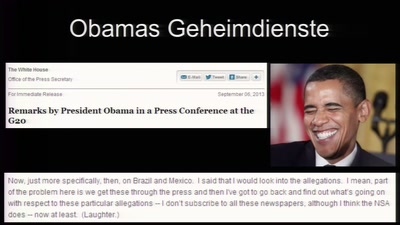
117 min
Fnord News Show
Der schonungslose Realitätsabgleich mit…

126 min
Logbuch:Netzpolitik 466
Die Ibiza-Affäre und ihre Folgen

54 min
How (not) to build autonomous robots
Fables from building a startup in Silicon Valley

58 min
Switches Get Stitches
Industrial System Ownership

49 min
Dissecting VoLTE
Exploiting Free Data Channels and Security Problems

60 min
The Critical Making Movement
How using critical thinking in technological practice can…

57 min
Everything you want to know about x86 microcode, but might have been afraid to ask
An introduction into reverse-engineering x86 microcode and…

61 min
Programming FPGAs with PSHDL
Let's create the Arduino for FPGAs

51 min
How to contribute to make open hardware happen
Mooltipass, Openpandora/Pyra and Novena/Senoko: how I…

55 min
Inside Field Station Berlin Teufelsberg
The story of the NSA listening post – told by an ex-SIGINT…

58 min
Self-encrypting deception
weaknesses in the encryption of solid state drives (SSDs)

63 min
Don't stop 'til you feel it
Artistic interventions in climate change

62 min
The Internet (Doesn't) Need Another Security Guide
Creating Internet Privacy and Security Resources That Don't…

63 min
goto fail;
exploring two decades of transport layer insecurity
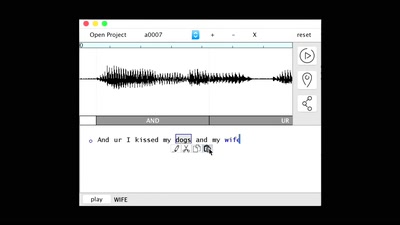
57 min