Search for "Ines" returned 2840 results
28 min
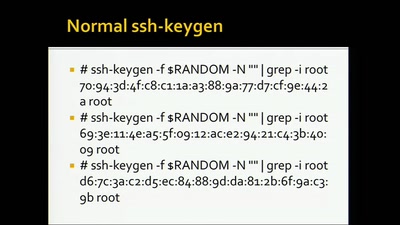
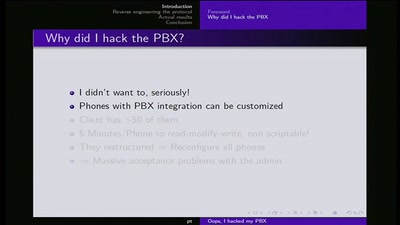
Ooops I hacked my PBX
Why auditing proprietary protocols matters

59 min
Quantum of Science
How quantum information differs from classical

62 min
Bionic Ears
Introduction into State-of-the-Art Hearing Aid Technology
57 min
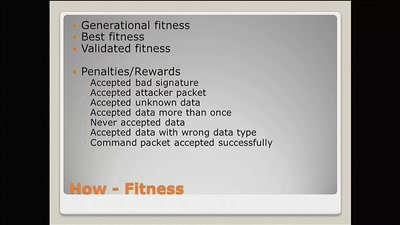
Evolving custom communication protocols
Hell Yeah, it's rocket science
75 min
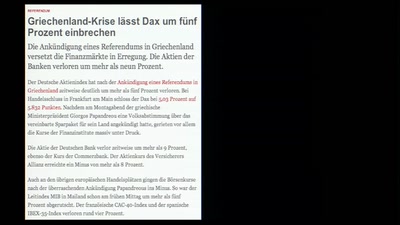
Fnord-Jahresrückblick
von Atomendlager bis Zensus

75 min
Fnord-Jahresrückblick
von Atomendlager bis Zensus

59 min
Almighty DNA?
Was die Tatort-Wahrheitsmaschine mit Überwachung zu tun hat
34 min
NOC Review
NOC Review about the Camp 2011 and the 28C3

57 min
Politik hacken
Kleine Anleitung zur Nutzung von Sicherheitslücken…
57 min
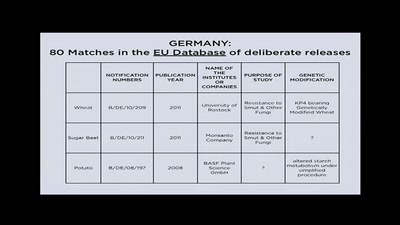
Eating in the Anthropocene
Transgenic Fish, Mutagenic Grapefruits and Space Potatoes
52 min
From Press Freedom to the Freedom of information
Why every citizen should be concerned
56 min
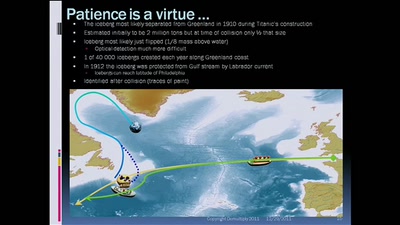
The future of cryptology: which 3 letters algorithm(s) could be our Titanic?
RMS Olympic, RMS Titanic, HMHS Britannic vs Discrete…

61 min
Electronic money: The road to Bitcoin and a glimpse forward
How the e-money systems can be made better

41 min
DC+, The Protocol
Technical defense against data retention law

52 min
The engineering part of social engineering
Why just lying your way in won't get you anywhere
40 min
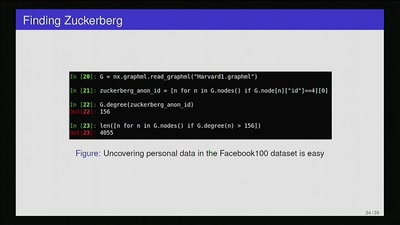
Privacy Invasion or Innovative Science?
Academia, social media data, and privacy

62 min
Post Memory Corruption Memory Analysis
Automating exploitation of invalid memory writes

49 min
Does Hacktivism Matter?
How the Btx hack changed computer law-making in Germany

59 min
Deceiving Authorship Detection
Tools to Maintain Anonymity Through Writing Style & Current…
60 min
What is WhiteIT and what does it aim for?
Why you probably want to be concerned about it and similiar…

55 min