Search for "T Arrow" returned 182 results

32 min
History and implications of DRM
From tractors to Web standards
54 min
Unsupervised Pleasures
Intersectional Language Models for Queer Futures
52 min
No Body's Business But Mine, a dive into Menstruation Apps
The Not-So Secret Data Sharing Practices Of Menstruation…

56 min
Reality Check! Basel/Lagos?? In virtual reality?
An African tale of art, culture and technology
59 min
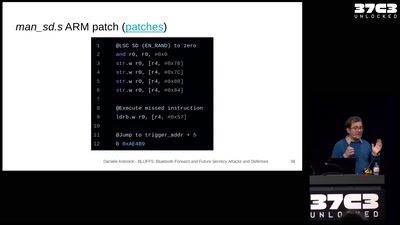
BLUFFS: Bluetooth Forward and Future Secrecy Attacks and Defenses
Breaking and fixing the Bluetooth standard. One More Time.
60 min
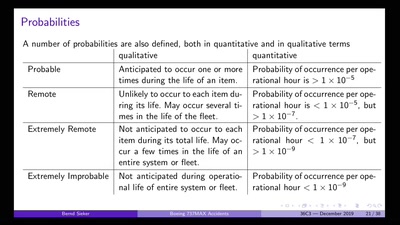
Boeing 737MAX: Automated Crashes
Underestimating the dangers of designing a protection system
31 min
Nerds in the news
Spending a year coding in a newsroom

42 min
A world without blockchain
How (inter)national money transfers works
65 min
Rocket science – how hard can it be?
First steps into space with sounding rockets

47 min
Bug class genocide
Applying science to eliminate 100% of buffer overflows

57 min
The Layman's Guide to Zero-Day Engineering
A demystification of the exploit development lifecycle
46 min
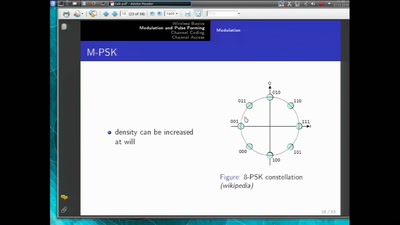
Basics of Digital Wireless Communication
introduction to software radio principles

60 min
Why is GPG "damn near unusable"?
An overview of usable security research
60 min
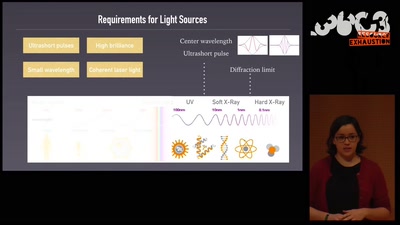
An ultrashort history of ultrafast imaging
Featuring the shortest movies and the largest lasers

64 min
Decoding the LoRa PHY
Dissecting a Modern Wireless Network for the Internet of…
62 min
Getting software right with properties, generated tests, and proofs
Evolve your hack into robust software!

59 min
Financial surveillance
Exposing the global banking watchlist
38 min