Search for "Victor Toso" returned 173 results

49 min
Toward a Cognitive "Quantified Self"
Activity Recognition for the Mind

41 min
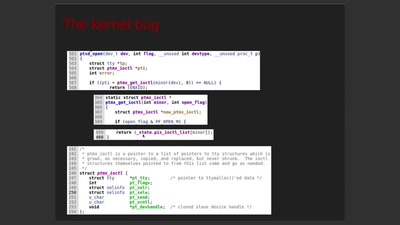
Breathing Life into Legacy: An Open-Source Emulator of Legacy Apple Devices
A Dive into Reverse Engineering and Understanding the iPod…
40 min
Never Forgetti
a didactic live-gaming performance about dying women across…

56 min
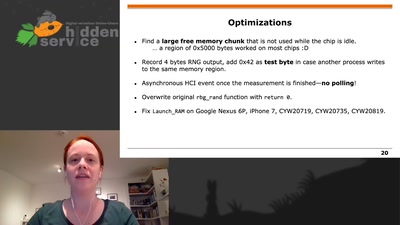
eMMC hacking, or: how I fixed long-dead Galaxy S3 phones
A journey on how to fix broken proprietary hardware by…

64 min
Cory Doctorow – Fireside Chat
Reading and Q&A

48 min
REXUS/BEXUS - Rocket and Balloon Experiments for University Students
How to bring student experiments into space.

60 min
Lockpicking in the IoT
...or why adding BTLE to a device sometimes isn't smart at…

64 min
Source Code and Cross-Domain Authorship Attribution
The Role of Stylometry in Privacy
55 min
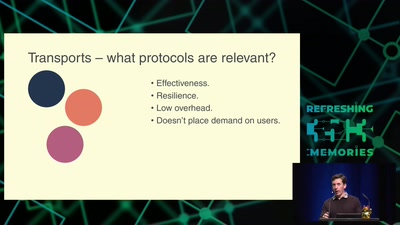
Cat & Mouse: Evading the Censors in 2018
Preserving access to the open Internet with circumvention…
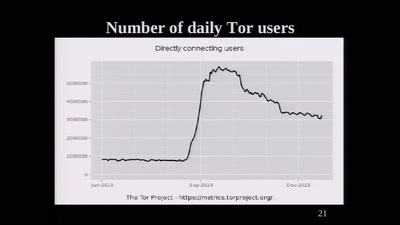
62 min
The Tor Network
We're living in interesting times

58 min
Glitching For n00bs
A Journey to Coax Out Chips' Inner Secrets

30 min
On Computing Numbers, with an Application to Problems of our Society
Journalism ♥ Computer Science

60 min
osmo-gmr: What's up with sat-phones ?
Piecing together the missing bits
60 min
Desperately Seeking Susy
A farewell to a bold proposal?
61 min
How to Hack Your Way to Space
Bringing the Hacker Mindset to the Space Ecosphere - The…

57 min