Search for "maggic" returned 357 results

60 min
Quantum Cryptography
from key distribution to position-based cryptography

60 min
Intel Management Engine deep dive
Understanding the ME at the OS and hardware level

46 min
SELECT code_execution FROM * USING SQLite;
--Gaining code execution using a malicious SQLite database

55 min
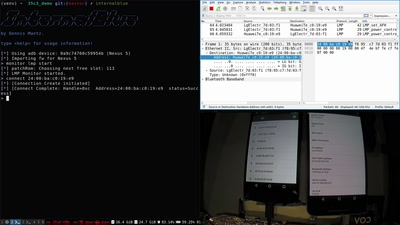
Fuzzing the phone in the iPhone
D-d-d-di-di-d-d-di-d-di-d-di-d-dimm!

54 min
Kernel Tracing With eBPF
Unlocking God Mode on Linux
61 min
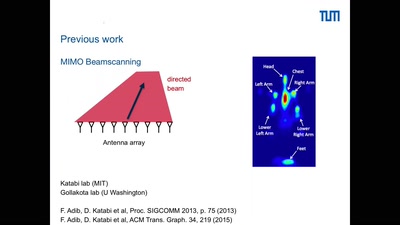
Holography of Wi-Fi radiation
Can we see the stray radiation of wireless devices? And…

60 min
Low Cost High Speed Photography
Using microcontrollers to capture the blink of an eye for…

29 min
Infocalypse now: P0wning stuff is not enough
Several failure modes of the hacker scene

56 min
eMMC hacking, or: how I fixed long-dead Galaxy S3 phones
A journey on how to fix broken proprietary hardware by…

59 min
Pointing Fingers at 'The Media'
The Bundestagswahl 2017 and Rise of the AfD
55 min
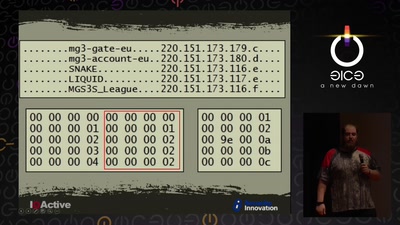
Cyber Necromancy
Reverse Engineering Dead Protocols

29 min