Search for "sECuRE" returned 791 results
45 min
Uyuni Saltboot - automated image deployment and lifecycle with Uyuni
Deploying filesystem images on real hardware or VMs…

46 min
Counselling Mischief as Thought Crime
Social Networks, Free Speech and the Criminalization of…

59 min
Security of the IC Backside
The future of IC analysis

63 min
Transparency and Privacy
The 7 Laws of Identity and the Identity Metasystem
62 min
Cryptocurrency Hardware Wallets
Building the First Monero Hardware Wallet

55 min
Revisiting SSL/TLS Implementations
New Bleichenbacher Side Channels and Attacks
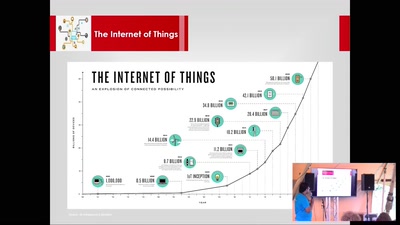
36 min
Smart Home Security with Tor
Using TOR for securing Smart Homes from prying eyes

46 min
Honeymonkeys
Chasing hackers with a bunch of monkeys
47 min
Distributed Actor System with Rust
Learn about the building blocks of a network application

100 min
The Fine Art of Hari Kari (.JS)
And Other Approaches For The Strange Reality Of Web Defense

60 min