Search for "sven" returned 2148 results

59 min
We should share our secrets
Shamir secret sharing: How it works and how to implement it

60 min
On the insecure nature of turbine control systems in power generation
A security study of turbine control systems in power…
36 min
Wheel of Fortune
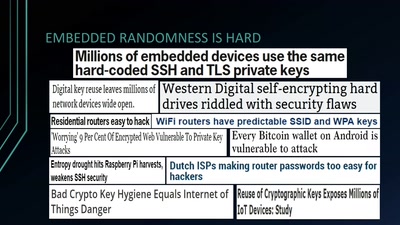
Analyzing Embedded OS Random Number Generators

47 min
Hardening hardware and choosing a #goodBIOS
Clean boot every boot - rejecting persistence of malicious…

58 min
PLC-Blaster
Ein Computerwurm für PLCs

64 min
We only have one earth
A case for expansionistic space policy

44 min
ASLR on the line
Practical cache attacks on the MMU

61 min
Uncaging Microchips
Techniques for Chip Preparation
65 min
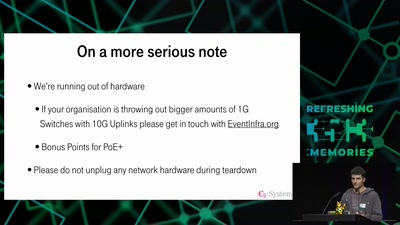
35C3 Infrastructure Review
Up and to the right: All the statistics about this event…
53 min
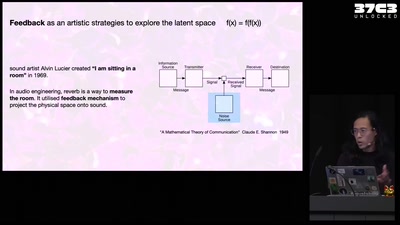
Self-cannibalizing AI
Artistic Strategies to expose generative text-to-image…
60 min
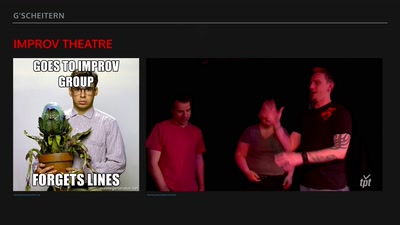
G’scheitern
The art of failure taught by improv theatre

61 min
Ten years after ‚We Lost The War‘
The future does not look much brighter than ten years ago.…

63 min
Building Custom Pinball Machines
What you need and how it works. An experiences report

61 min
The architecture of a street level panopticon
How drones, IMSI Catchers, and cameras are shaping our…

41 min
Why Railway Is Safe But Not Secure
Security Of Railway Communication Protocols
66 min