Search for "Sven" returned 2036 results
59 min
Internet of Fails
Where IoT has gone wrong
47 min
Going Deep Underground to Watch the Stars
Neutrino Astronomy with Hyper-Kamiokande

61 min
Code Pointer Integrity
... or how we battle the daemons of memory safety
58 min
Confessions of a future terrorist
A rough guide to over-regulating free speech with…

32 min
What's It Doing Now?
The Role of Automation Dependency in Aviation Accidents

61 min
Computational Meta-Psychology
An Artificial Intelligence exploration into the creation of…

54 min
World War II Hackers
Stalin's best men, armed with paper and pen

58 min
When hardware must „just work“
An inside look at x86 CPU design

59 min
Hacking EU funding for a decentralizing FOSS project
Understanding and adapting EU legal guidelines from a FOSS…

54 min
Attacking Chrome IPC
Reliably finding bugs to escape the Chrome sandbox
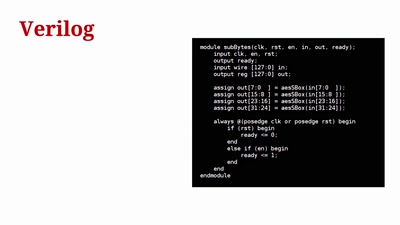
59 min
Towards General Purpose Reconfigurable Computing on Novena
FPGAs for Everybody with Novena

39 min
ID Cards in China: Your Worst Nightmare
In China Your ID Card Knows Everything

30 min
All Our Shared Spectrum Are Belong to Us
Visualizing WLAN Channel Usage on OpenWRT
44 min