Search for "jk" returned 2278 results

58 min
When hardware must „just work“
An inside look at x86 CPU design

29 min
The Pirate Cinema
Creating mash-up movies by hidden activity and geography of…

55 min
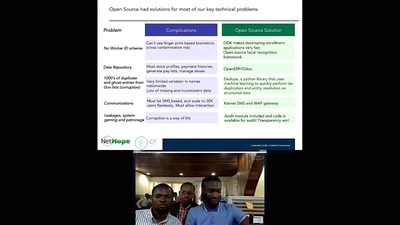
The Gospel of IRMA
Attribute Based Credentials in Practice

39 min
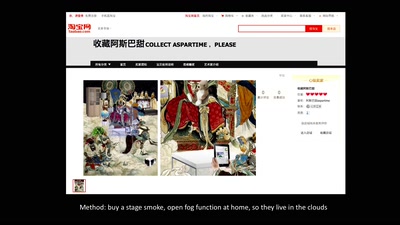
ID Cards in China: Your Worst Nightmare
In China Your ID Card Knows Everything
58 min
CHINTERNET ART
Creativity, Archives & Digital Media from the Chinese…

49 min
BREACH in Agda
Security notions, proofs and attacks using dependently…

66 min
Die Drohnenkriege
Kriegsführung der Zukunft?
46 min
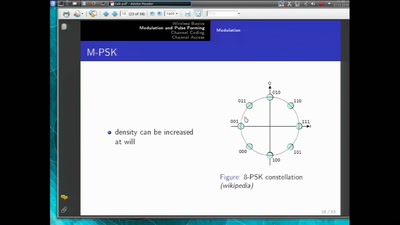
Basics of Digital Wireless Communication
introduction to software radio principles
33 min
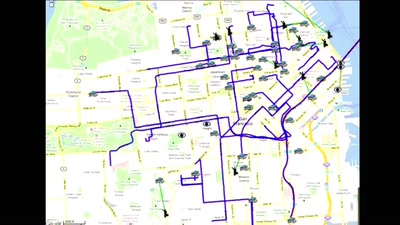
Space making/space shaping
How mapping creates space, shapes cities and our view of…

33 min
Global Civil Society Under Attack
Reports from the Frontlines

55 min
The DROWN Attack
Breaking TLS using SSLv2
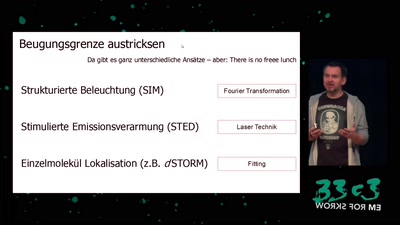
60 min
Es sind die kleinen Dinge im Leben
von Mikroskopen, Wahrnehmung und warum das kaum jemanden…

51 min
Uncovering vulnerabilities in Hoermann BiSecur
An AES encrypted radio system

49 min
Toward a Cognitive "Quantified Self"
Activity Recognition for the Mind

42 min