Search for "Sven" returned 2036 results
59 min
Towards General Purpose Reconfigurable Computing on Novena
FPGAs for Everybody with Novena
38 min
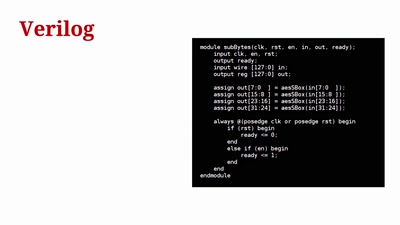
A deep dive into the world of DOS viruses
Explaining in detail just how those little COM files…

29 min
Infocalypse now: P0wning stuff is not enough
Several failure modes of the hacker scene

60 min
Free Software and Hardware bring National Sovereignty
Gaza as a case study
47 min
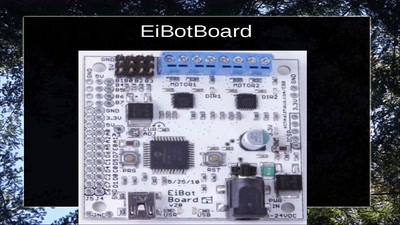
Hillbilly Tracking of Low Earth Orbit
Repurposing an Inmarsat Dish
46 min
What The Fax?!
Hacking your network likes it's 1980 again
60 min
So you want to build a satellite?
How hard can it be? An introduction into CubeSat development

60 min
Adventures in Reverse Engineering Broadcom NIC Firmware
Unlocking a system with 100% open source firmware
27 min
One year of securitarian drift in France
From the Bill on Intelligence to the State of Emergency

39 min
The automobile as massive data gathering source and the consequences for individual…
The next big privacy heist

58 min
Hack_Curio
Decoding The Cultures of Hacking One Video at a Time

31 min
PUFs, protection, privacy, PRNGs
an overview of physically unclonable functions

53 min