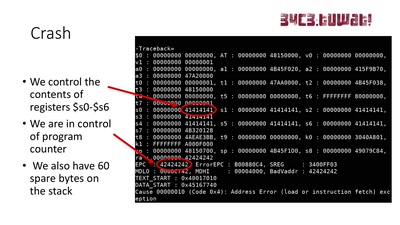
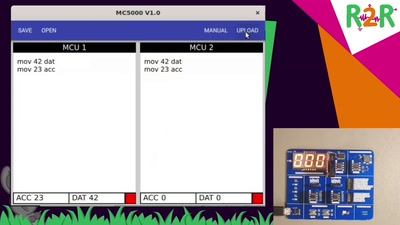
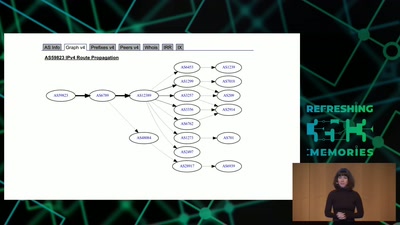
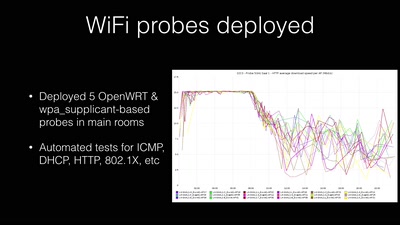
Search for "xif" returned 1978 results

32 min
Finding the Weak Crypto Needle in a Byte Haystack
Automatic detection of key-reuse vulnerabilities

49 min
Electromagnetic Threats for Information Security
Ways to Chaos in Digital and Analogue Electronics
33 min
Computer Science in the DPRK
A view into technology on the other side of the world

43 min
This is NOT a proposal about mass surveillance!
Analysing the terminology of the UK’s Snooper’s Charter

37 min
The foodsaving grassroots movement
How cooperative online structures can facilitate…

36 min
Accessible input for readers, coders, and hackers
From eyelid blinks to speech recognition

32 min
Technology and Mass Atrocity Prevention
Overview on Current Efforts - We Need Moar H4x0rs?!

32 min
Modern key distribution with ClaimChain
A decentralized Public Key Infrastructure that supports…

59 min
Hacking EU funding for a decentralizing FOSS project
Understanding and adapting EU legal guidelines from a FOSS…

60 min
Hacking Reality
Mixed Reality and multi-sensory communication

62 min
The Price Of Dissent
The surveillance state & modern day COINTELPRO tactics

43 min
#NoPNR – Let’s kill the next Data Retention Law
How to Stop the Dubious Use of Passenger Name Records by…

31 min