Search for "CAGE" returned 2827 results

28 min
Long war tactics
or how we learned to stop worrying and love the NSA
37 min
DON’T PANIC
bytes, blocks, bugs

40 min
Fuzz Everything, Everywhere, All at Once
Advanced QEMU-based fuzzing

30 min
Rowhammer.js: Root privileges for web apps?
A tale of fault attacks on DRAM and attacks on CPU caches
46 min
The Mission of the MV Louise Michel
"Feminism will be anti-racist or it won´t be"
62 min
The Ghost in the Machine
An Artificial Intelligence Perspective on the Soul

62 min
Calafou, postcapitalist ecoindustrial community
Building a space for grassroots sustainable technology…
42 min
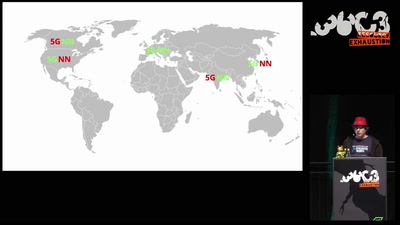
5G & Net Neutrality
Status of the Net Neutrality Reform in Europe
55 min
Cat & Mouse: Evading the Censors in 2018
Preserving access to the open Internet with circumvention…
29 min