Search for "Sec" returned 2701 results

55 min
What could possibly go wrong with <insert x86 instruction here>?
Side effects include side-channel attacks and bypassing…

60 min
Beyond Anti Evil Maid
Making it easier to avoid low-level compromise, and why…
31 min
openPower - the current state of commercial openness in CPU development
is there no such thing as open hardware?

48 min
Seidenstraße
The Making of…

42 min
Reverse engineering FPGAs
Dissecting FPGAs from bottom up, extracting schematics and…
31 min
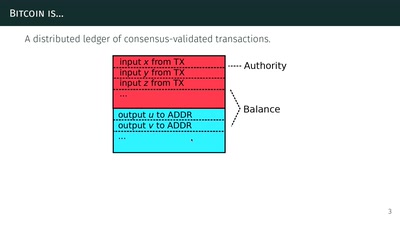
The Zcash anonymous cryptocurrency
or zero-knowledge succinct non-interactive arguments of…

20 min
Mastering the Maze
Unleashing Reinforcement Learning in Penetration Testing…
39 min
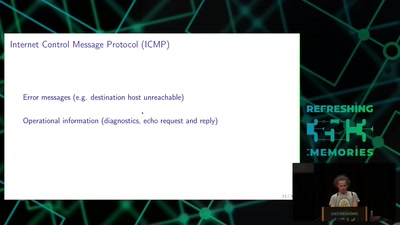
Transmission Control Protocol
TCP/IP basics

60 min
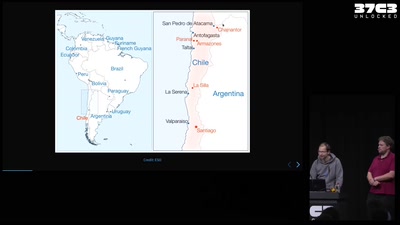
Profiling (In)justice
Disaggregating Data by Race and Ethnicity to Curb…
40 min
The Extremely Large Telescope (ELT)
Building the biggest optical telescope on earth

59 min
Say hi to your new boss: How algorithms might soon control our lives.
Discrimination and ethics in the data-driven society
41 min
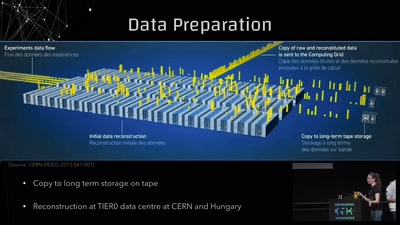
Conquering Large Numbers at the LHC
From 1 000 000 000 000 000 to 10: Breaking down 14 Orders…

31 min
A Tale of Two Leaks:
How Hackers Breached the Great Firewall of China
60 min
Lifting the Fog on Red Star OS
A deep dive into the surveillance features of North Korea's…

63 min
Synthetic Sentience
Can Artificial Intelligence become conscious?
41 min