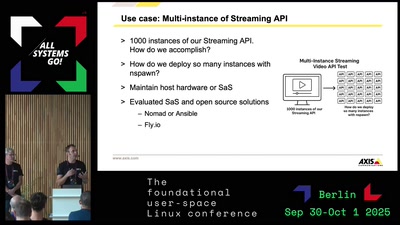
Search for "kay" returned 3827 results

45 min
Triggering Deep Vulnerabilities Using Symbolic Execution
Deep program analysis without the headache

51 min
Reverse Engineering the MOS 6502 CPU
3510 transistors in 60 minutes
46 min
Making machines that make
rapid prototyping of digital fabrication and…
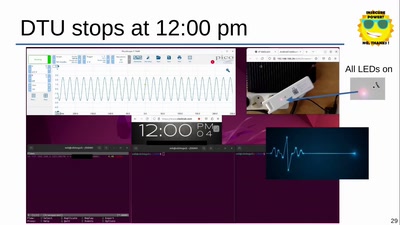
39 min
Decentralized energy production: green future or cybersecurity nightmare?
The cybersecurity dark side of solar energy when clouds are…

66 min
BOLSONARO IS AN ENVIRONMENTAL CATASTROPH!
How the rise of bolsonsarism culminate in the Burning of…
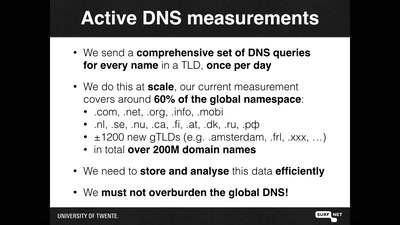
58 min
OpenINTEL: digging in the DNS with an industrial size digger
I measured 60% of the DNS, and I found this
33 min
Open Source: A question of national and global security
What will you do when things go bad? Taking precautions in…
28 min