Search for "Sven" returned 2036 results
46 min
Basics of Digital Wireless Communication
introduction to software radio principles
60 min
Unpatchable
Living with a vulnerable implanted device

60 min
Everything you always wanted to know about Certificate Transparency
(but were afraid to ask)

60 min
The Critical Making Movement
How using critical thinking in technological practice can…
40 min
Handsfree assistive technology
My technology portfolio to enable work, life, smart home…

60 min
Beyond Anti Evil Maid
Making it easier to avoid low-level compromise, and why…

54 min
What Price the Upload Filter?
The history and costs of government exceptional access

40 min
Intercoms Hacking
Call the frontdoor to install your backdoors
64 min
On the Security and Privacy of Modern Single Sign-On in the Web
(Not Only) Attacks on OAuth and OpenID Connect
66 min
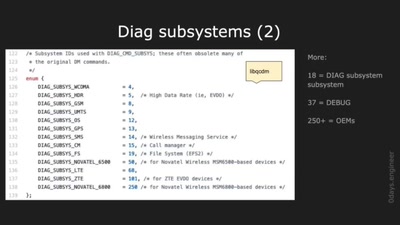
Advanced Hexagon Diag
Harnessing diagnostics for baseband vulnerability research

30 min
Electroedibles
Open Source Hardware for Smart Candies

55 min
Inside Field Station Berlin Teufelsberg
The story of the NSA listening post – told by an ex-SIGINT…

25 min
»Hard Drive Punch«
Destroying data as a performative act

54 min