Search for "jk" returned 2285 results

58 min
Switches Get Stitches
Industrial System Ownership
60 min
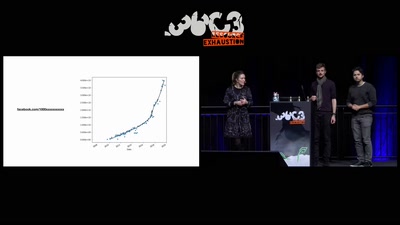
Inside the Fake Like Factories
How thousands of Facebook, You Tube and Instagram pages…

55 min
Attribution revolution
Turning copyright upside-down with metadata

55 min
Inside Field Station Berlin Teufelsberg
The story of the NSA listening post – told by an ex-SIGINT…

33 min
Kampf dem Abmahnunwesen
Wider die automatisierte Rechtsdurchsetzung

49 min
BREACH in Agda
Security notions, proofs and attacks using dependently…
45 min
SCADA - Gateway to (s)hell
Hacking industrial control gateways

57 min
A Dozen Years of Shellphish
From DEFCON to the DARPA Cyber Grand Challenge

60 min
30C3 Opening Event
Welcome to the 30th Chaos Communication Congress
25 min
Saving the World with Space Solar Power
or is it just PEWPEW?!

55 min
The DROWN Attack
Breaking TLS using SSLv2
60 min
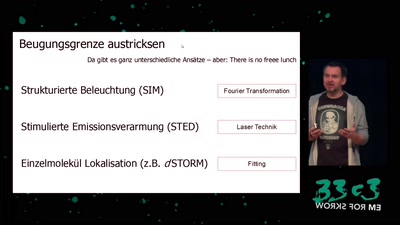
Es sind die kleinen Dinge im Leben
von Mikroskopen, Wahrnehmung und warum das kaum jemanden…

32 min
Fuck Dutch mass-surveillance: let's have a referendum!
Forcing the Netherlands to publicly debate privacy and the…
59 min