Search for "JO" returned 10053 results
46 min
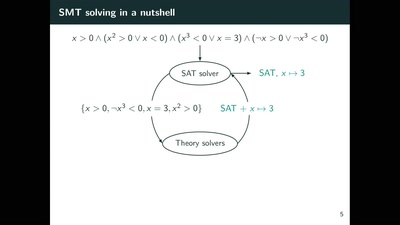
Satisfiability Modulo Theories
Using OS to solve hard problems
60 min
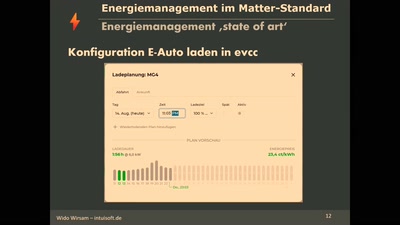
Energiemanagement im Matter-Standard
So funktioniert Energiemanagement in Matter ab Version 1.3
53 min
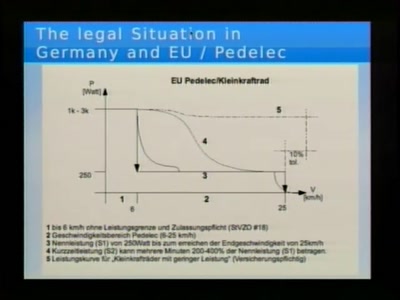
21st Century digital Bikes
No Gas, No Fee or Tax, No Driver License, what's possible…

32 min
Netboot21: Bootloaders in the 21st Century
User-space bootloaders with LinuxBoot

31 min
libcapsule
segregated loading of dynamic libraries
26 min
Container Run-times and Fun-times
Using systemd inside a container @FB
43 min
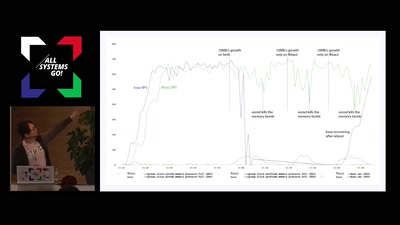
Resource Control @FB
Functional resource control using cgroup2
36 min