Search for "mh" returned 2881 results

59 min
We should share our secrets
Shamir secret sharing: How it works and how to implement it
60 min
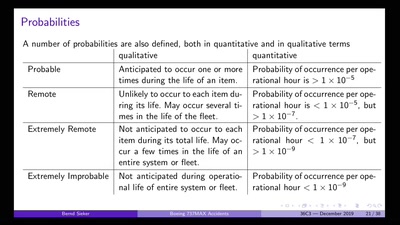
Boeing 737MAX: Automated Crashes
Underestimating the dangers of designing a protection system

30 min
Privacy and Consumer Markets
Reversing the Surveillance Business Model

95 min
Platform System Interface
Design und Evaluation holistischer Computerarchitektur

58 min
Self-encrypting deception
weaknesses in the encryption of solid state drives (SSDs)
26 min
Plants & Machines
Food replicating Robots from Open Source Technologies

33 min
Turing Complete User
What can be done to protect the term, the notion and the…

43 min
Tractors, Rockets and the Internet in Belarus
How belarusian authoritarian regime is using technologies…

51 min
How to contribute to make open hardware happen
Mooltipass, Openpandora/Pyra and Novena/Senoko: how I…

37 min
Hacking (with) a TPM
Don't ask what you can do for TPMs, Ask what TPMs can do…

39 min
The automobile as massive data gathering source and the consequences for individual…
The next big privacy heist

49 min
BREACH in Agda
Security notions, proofs and attacks using dependently…

61 min