Search for "olf" returned 7379 results
62 min
The movements against state-controlled Internet in Turkey
A short account of its history and future challenges
44 min
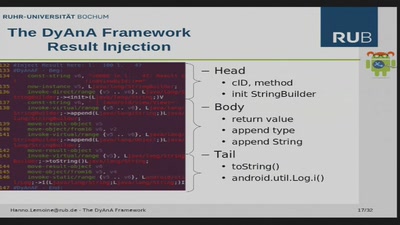
Dynamic Malware Analysis on Android Phones
Presentation of the DyAnA Framework (Dynamic Android…

63 min
Print Me If You Dare
Firmware Modification Attacks and the Rise of Printer…
61 min
Hacking the universe
When strings are super and not made of characters
37 min
Reproducible Builds - where do we want to go tomorrow?
We've made lots of progress, but we are still far from our…
59 min
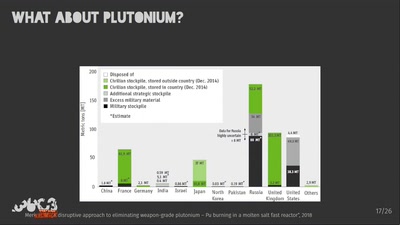
Megatons to Megawatts
Military warheads as a source of nuclear fuel

32 min
What's It Doing Now?
The Role of Automation Dependency in Aviation Accidents

26 min
Don't scan, just ask
A new approach of identifying vulnerable web applications
53 min
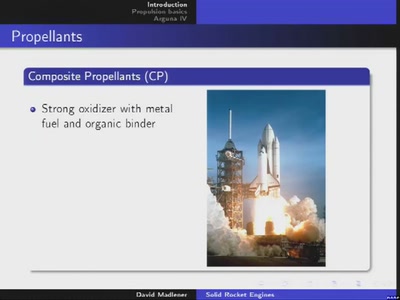
Solid rocket engines
Design and implementation of engines with solid propellant
79 min
Stream: Fnord-Jahresrückblick 2009
German / English version of the Fnord-Jahresrückblick 2009.
46 min
Making machines that make
rapid prototyping of digital fabrication and…
15 min
openSUSE on the Mainframe
The Future of community distributions on IBM Z

41 min
Deaths per TWh
The Price of Energy and Reducing CO2 Emissions

59 min
System-Level Transactions with picotm
The Days of Plenty Are Yet to Come

60 min
When Tech MIMICS Reality
Identity and Agency In the Age of Algorithms

50 min
Ceph Explained - With Raspberry Pis
Demonstration of Ceph on a Raspberry Pi cluster

59 min
Visiting The Bear Den
A Journey in the Land of (Cyber-)Espionage
35 min
Uncertainty
and the Art's Response to Regulations of Control
60 min
G’scheitern
The art of failure taught by improv theatre

58 min
07KINGSTON25 JAMAICA: MALARIA UPDATE Dispatches from Fort Meade
Reporting on the secret trial of Chelsea Manning
32 min
Coding your body
How to decipher the messages of your body

57 min
Page Fault Liberation Army or Gained in Translation
a history of creative x86 virtual memory uses

19 min

