Search for "Andy" returned 7488 results
47 min
The Realm of Too Many Options
Write, record, mix and actually finish your music
24 min
From Physical to Cloud to Container
One system to deploy and manage them all

20 min
HTCPCP - Networking your Coffeepot
IoT done right for fun and no profit

59 min
8 Years of Config Management
a journey through one company's challenges and learnings

35 min
Weaponized Social
Understanding and tools to mitigate network-scale violences
98 min
Towards automatic end to end mail encryption
mail encryption overview and hands-on Autocrypt sessions

43 min
Pirate Radio
Running a Station and Staying on the Air

30 min
Closing Event
So long and thanks for all the fish

47 min
What you thought you knew about C
Impacts of undefined behaviour and other C oddities

48 min
All Tomorrow's Condensation
A steampunk puppet extravaganza by monochrom and friends
![for women in "${tech[@]}"; do](https://static.media.ccc.de/media/conferences/camp2015/6774-hd.jpg)
26 min
for women in "${tech[@]}"; do
Let's talk, share and learn from each other.

21 min
Closing Event
Good Bye and have a safe trip home!
58 min
Advanced memory forensics: The Cold Boot Attacks
Recovering keys and other secrets after power off
60 min
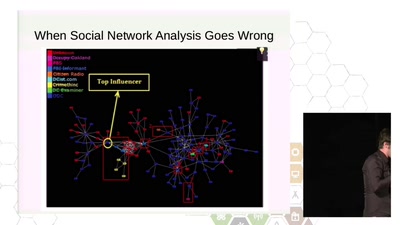
Resisting Surveillance: it's is not just about the metadata
The infiltration and physical surveillance of social…

59 min
Say hi to your new boss: How algorithms might soon control our lives.
Discrimination and ethics in the data-driven society

61 min
Trustworthy secure modular operating system engineering
fun(ctional) operating system and security protocol…
56 min
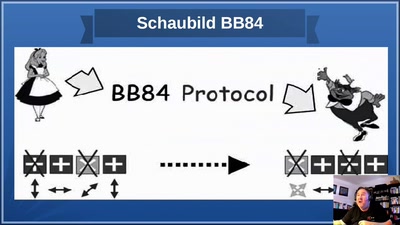
God does not play dice!
an introduction to quantum cryptography for sysadmins and…

60 min
Intel Management Engine deep dive
Understanding the ME at the OS and hardware level
74 min
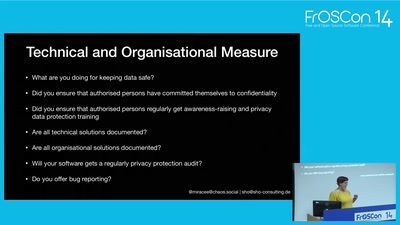
Privacy by design
how to code GDPR and e-privacy regulation safe

25 min
30 seconds to Code
Streamlining development setups with Docker and Open Build…

66 min
Podjournalism
The Role of Podcasting in Critical and Investigative…
64 min
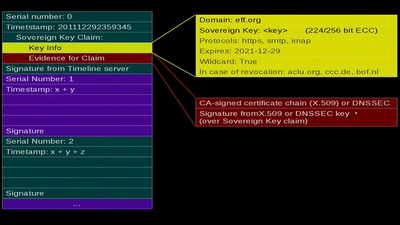
Sovereign Keys
A proposal for fixing attacks on CAs and DNSSEC

52 min
The Youth Hostel
An odyssey in the margins of software and paper

34 min
