Search for "JO" returned 10053 results
43 min
Resource Control @FB
Functional resource control using cgroup2
36 min
Is my system fast?
An introduction of some tools that help to answer this…
57 min
Zehn Big Brother Awards in .at
Rückblick über eine bewegte Zeit

60 min
The Trust Situation
Why the idea of data protection slowly turns out to be…

39 min
Scalable Swarm Robotics
Formica: a cheap, open research platform

62 min
Security and anonymity vulnerabilities in Tor
Past, present, and future

48 min
The Privacy Workshop Project
Enhancing the value of privacy in todays students view

61 min
Lightning Talks Day4
4 minutes of fame
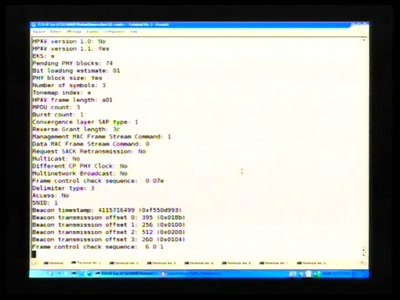
50 min
FAIFA: A first open source PLC tool
PowerLineCommunications has now their open source tool

65 min
Terrorist All-Stars
Some cases of terrorism around the world that are not…

44 min