Search for "Jason" returned 211 results
58 min
The Ultimate Acorn Archimedes talk
Everything about the Archimedes computer (with zero…

58 min
Switches Get Stitches
Industrial System Ownership
39 min
Should e-voting experience of Estonia be copied?
Observer report of 2023 parliamentary elections

58 min
How risky is the software you use?
CITL: Quantitative, Comparable Software Risk Reporting

42 min
Rettet uns die KI?
Über die Zukunft der digitalen Inklusion

37 min
Hacking (with) a TPM
Don't ask what you can do for TPMs, Ask what TPMs can do…
48 min
10 Years of Fun with Embedded Devices
How OpenWrt evolved from a WRT54G firmware to an universal…

40 min
Fuzz Everything, Everywhere, All at Once
Advanced QEMU-based fuzzing
29 min
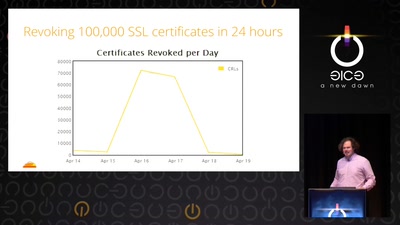
Heartache and Heartbleed: The insider’s perspective on the aftermath of Heartbleed
The untold story of what really happened, how it was…

40 min
An introduction to Firmware Analysis
Techniques - Tools - Tricks

42 min
NEW IMPORTANT INSTRUCTIONS
Real-world exploits and mitigations in Large Language Model…

38 min
Content take-downs: Who cleans the internet?
EU plans to swipe our freedom of expression under the carpet

55 min