Search for "Victor Toso" returned 173 results

60 min
APT Reports and OPSEC Evolution, or: These are not the APT reports you are looking for
How advanced threat actors learn and change with innovation…
38 min
Unpacking the compromises of Aadhaar, and other digital identities inspired by it
Governments around the world are implementing digital…

63 min
goto fail;
exploring two decades of transport layer insecurity

59 min
We should share our secrets
Shamir secret sharing: How it works and how to implement it

44 min
Disclosure DOs, Disclosure DON'Ts
Pragmatic Advice for Security Researchers

64 min
It Always Feels Like the Five Eyes Are Watching You
Five Eyes’ Quest For Security Has Given Us Widespread…

46 min
Taking a scalpel to QNX
Analyzing & Breaking Exploit Mitigations and Secure Random…

69 min
cryptocurrencies, smart contracts, etc.: revolutionary tech?
short answer: Yes!

60 min
My Robot Will Crush You With Its Soft Delicate Hands!
How to design and fabricate soft robots using everyday…
58 min
Script Your Car!
Using existing hardware platforms to integrate python into…

60 min
HAL - The Open-Source Hardware Analyzer
A dive into the foundations of hardware reverse engineering…
61 min
Rocket Kitten: Advanced Off-the-Shelf Targeted Attacks Against Nation States
A Deep Technical Analysis
59 min
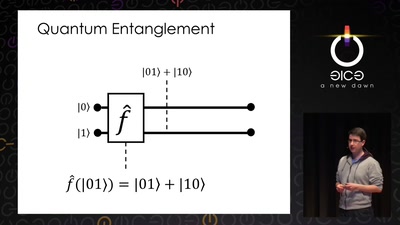
Let's build a quantum computer!
Understanding the architecture of a quantum processor
91 min
What the World can learn from Hongkong
From Unanimity to Anonymity

58 min