Search for "Dan" returned 11395 results

55 min
Attribution revolution
Turning copyright upside-down with metadata

33 min
Global Civil Society Under Attack
Reports from the Frontlines

95 min
The Time is Right
Ein Science-Fiction-Theaterstück
32 min
Eye Wear Computing
Augmenting the Human Mind
62 min
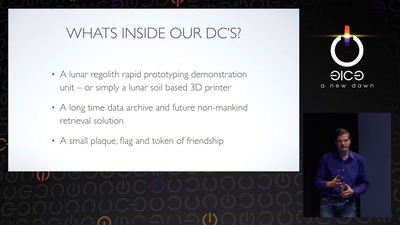
Space Hacker
Uploading rover...

55 min
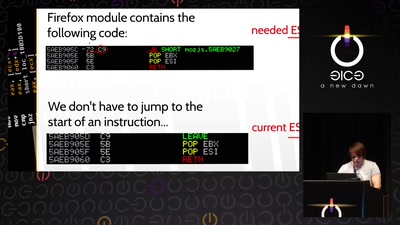
Revisiting SSL/TLS Implementations
New Bleichenbacher Side Channels and Attacks

30 min
The Magical Secrecy Tour
A Bus Trip into the Surveillance Culture of Berlin One Year…

54 min
AMD x86 SMU firmware analysis
Do you care about Matroshka processors?

62 min
Tell no-one
A century of secret deals between the NSA and the telecom…
55 min
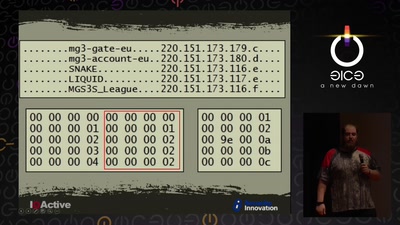
Cyber Necromancy
Reverse Engineering Dead Protocols

45 min
Serenität – Anleitung zum Glücklichsein
Das Duo 'read & delete' präsentiert radikale philosophische…

63 min