Search for "olf" returned 7379 results
41 min
Introduction to (home) network security.
A beginner-friendly guide to network segmentation for…
58 min
OpenINTEL: digging in the DNS with an industrial size digger
I measured 60% of the DNS, and I found this

32 min
Is this the Mobile Gadget World We Created?
The story of the world's first socially responsible mobile…
52 min
Hybrid rocket engines
Design and implementation of rocket engines with two-phase…

62 min
I Control Your Code
Attack Vectors Through the Eyes of Software-based Fault…

26 min
ChokePointProject - Quis custodiet ipsos custodes?
Aggregating and Visualizing (lack of) Transparancy Data in…
51 min
iOS application security
A look at the security of 3rd party iOS applications
47 min
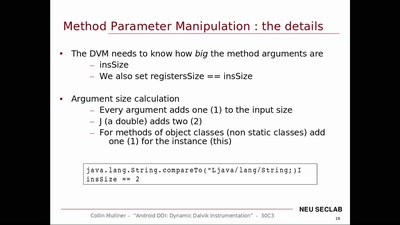
Android DDI
Dynamic Dalvik Instrumentation of Android Applications and…
47 min
Distributed Actor System with Rust
Learn about the building blocks of a network application
59 min
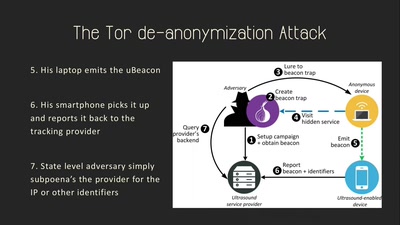
Talking Behind Your Back
On the Privacy & Security of the Ultrasound Tracking…
42 min
Terminator Genes and GURT - Biological Restrictions Management
Five Years after the announcement of a quasi moratorium

59 min
10GE monitoring live!
How to find that special one out of millions

52 min
Adventures in Mapping Afghanistan Elections
The story of 3 Ushahidi mapping and reporting projects.

61 min
Code Pointer Integrity
... or how we battle the daemons of memory safety
53 min
Crouching Powerpoint, Hidden Trojan
An analysis of targeted attacks from 2005 to 2007

48 min
The Privacy Workshop Project
Enhancing the value of privacy in todays students view

61 min
Computational Meta-Psychology
An Artificial Intelligence exploration into the creation of…

53 min
Eight rollouts a day keeping downtime away
The philosophy of shared space in a development environment

30 min
Love, CyBorgs, Art and Open Source – an artistic approach on how to stay golden
How to educate society through the language of art

45 min
Generating uniqueness
How generative art pushes the boundaries of intellectual…

58 min
Self-encrypting deception
weaknesses in the encryption of solid state drives (SSDs)

60 min
Fictional panel discussion: Let Nature Rule
Exploring solutions and impacts of automated environmental…
31 min
Growing Up Software Development
From Hacker Culture to the Software of the Future

57 min
“I feel like a criminal and I have to be god at the same time”
Perceptions of hackers and hacktivists on their…

62 min