Search for "Sven" returned 2036 results

60 min
Dieselgate – A year later
env stinks || exit
58 min
Script Your Car!
Using existing hardware platforms to integrate python into…

44 min
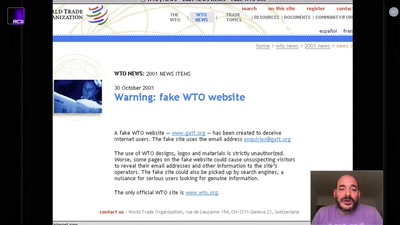
Disclosure DOs, Disclosure DON'Ts
Pragmatic Advice for Security Researchers

49 min
Key-logger, Video, Mouse
How to turn your KVM into a raging key-logging monster
29 min
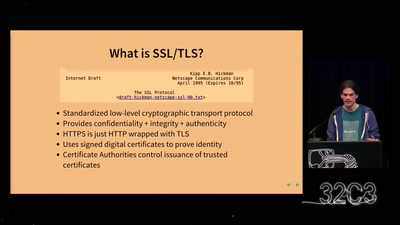
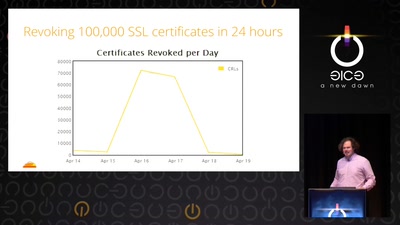
Heartache and Heartbleed: The insider’s perspective on the aftermath of Heartbleed
The untold story of what really happened, how it was…

57 min
Everything you want to know about x86 microcode, but might have been afraid to ask
An introduction into reverse-engineering x86 microcode and…

58 min
How risky is the software you use?
CITL: Quantitative, Comparable Software Risk Reporting

53 min
From Maxwell to antenna arrays
How 150 year old equations still help to communicate

36 min
Von Zebrastreifen, offenen Daten und verschlossenen Verwaltungen
Luxemburgs kreative Route zur Amtstransparenz

63 min
Reproducible Builds
Moving Beyond Single Points of Failure for Software…

19 min