Search for "jk" returned 2287 results
91 min
What the World can learn from Hongkong
From Unanimity to Anonymity
58 min
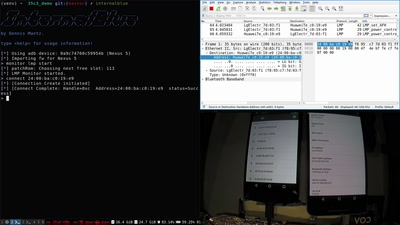
Operation Triangulation
What You Get When Attack iPhones of Researchers

61 min
Trustworthy secure modular operating system engineering
fun(ctional) operating system and security protocol…

59 min
De-anonymizing Programmers
Large Scale Authorship Attribution from Executable Binaries…

62 min
The Internet (Doesn't) Need Another Security Guide
Creating Internet Privacy and Security Resources That Don't…
59 min
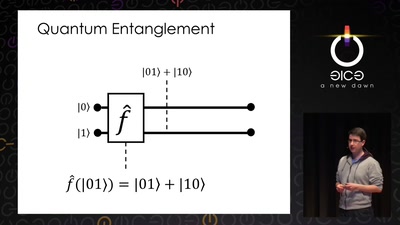
Let's build a quantum computer!
Understanding the architecture of a quantum processor

41 min
Locked up science
Tearing down paywalls in scholarly communication

40 min
Intercoms Hacking
Call the frontdoor to install your backdoors

60 min
The rise and fall of Internet voting in Norway
Evaluating a complex cryptographic implementation
25 min
Keys of Fury
Type In Beyond the Scrolling Horizon

48 min
Don't Ruck Us Too Hard - Owning Ruckus AP Devices
3 different RCE vulnerabilities on Ruckus Wireless access…

32 min
Craft, leisure, and end-user innovation
How hacking is conceived in social science research
40 min
Infrastructures in a horizontal farmers community
Human agreements, comunication infrastructures, services in…

55 min
ZombieLoad Attack
Leaking Your Recent Memory Operations on Intel CPUs

60 min
Quantum Cryptography
from key distribution to position-based cryptography

29 min
Infocalypse now: P0wning stuff is not enough
Several failure modes of the hacker scene

60 min
Adventures in Reverse Engineering Broadcom NIC Firmware
Unlocking a system with 100% open source firmware
61 min
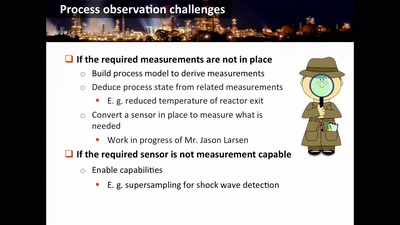
Damn Vulnerable Chemical Process
Exploitation in a new media

59 min