Search for "jk" returned 2287 results
58 min
RFID Treehouse of Horror
Hacking City-Wide Access Control Systems

51 min
Virtual Secure Boot
Secure Boot support in qemu, kvm and ovmf.

55 min
Graphs, Drones & Phones
The role of social-graphs for Drones in the War on Terror.
47 min
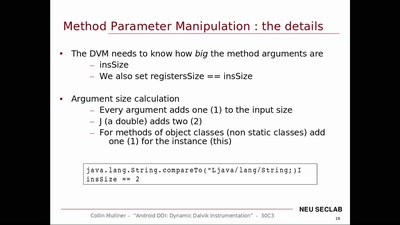
Android DDI
Dynamic Dalvik Instrumentation of Android Applications and…

48 min
REXUS/BEXUS - Rocket and Balloon Experiments for University Students
How to bring student experiments into space.

59 min
We should share our secrets
Shamir secret sharing: How it works and how to implement it
56 min
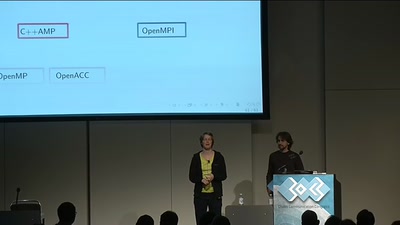
Rock' em Graphic Cards
Introduction to Heterogeneous Parallel Programming

60 min
From Computation to Consciousness
How computation helps to explain mind, universe and…

58 min
Virtual Machine Introspection
From the Outside Looking In

46 min
Climate Modelling
The Science Behind Climate Reports

62 min
radare demystified
after 1.0

59 min
How to teach programming to your loved ones
Enabling students over example-driven teaching

29 min