Search for "Andi" returned 7404 results
26 min
Der 33 Jahrerückblick
Technology and Politics in Congress Talks, from 1984 to now
52 min
Fragile development
Why Scrum sucks, and what you should be doing instead
62 min
dstat: plugin-based real-time monitoring system
How to correlate system counters and make your life easier

60 min
My Robot Will Crush You With Its Soft Delicate Hands!
How to design and fabricate soft robots using everyday…
49 min
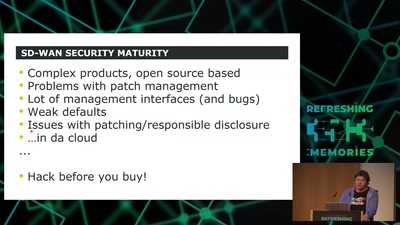
SD-WAN a New Hop
How to hack software defined network and keep your sanity?

52 min
SiliVaccine: North Korea's Weapon of Mass Detection
How I Learned to Stop Worrying and Love the Backdoor

60 min
A brain is not a computer
Insights into neurology and psychological behaviours…

60 min
The Hash Disaster
Recent Results on Cryptanalysis and their Implications on…

62 min
GUERRILLA.COM
How to mess with media, the market and life itself

60 min
Profiling (In)justice
Disaggregating Data by Race and Ethnicity to Curb…

49 min
Access to Knowledge
Copyright, Patents and Politics at the World Intellectual…
![NSFW: Di[CENSORED]s for privacy](https://static.media.ccc.de/media/events/SHA2017/49-hd.jpg)
28 min
NSFW: Di[CENSORED]s for privacy
Why not give hackers and agencies something to look at . .

29 min
Pegasus internals
Technical Teardown of the Pegasus malware and Trident…

48 min
Oil Into Digits
A short exploration of the relation between energy and…

33 min
Enabling Innovation in Europe
Hacker Spaces, Startups, and a new approach to social…

45 min
Secure Network Server Programming on Unix
Techniques and best practices to securely code your network…

68 min
"Spoilers, Reverse Green, DECEL!" or "What's it doing now?"
Thoughts on the Automation and its Human interfaces on…

60 min
The plain simple reality of entropy
Or how I learned to stop worrying and love urandom
61 min
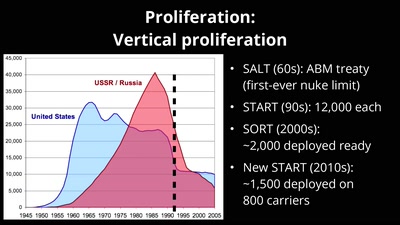
What Ever Happened to Nuclear Weapons?
Politics and Physics of a Problem That's Not Going Away
28 min
Accelerating Scientific Research through Spinning Out a Software Company
Our story about finding the balance between free and…

40 min
What is this? A machine learning model for ants?
How to shrink deep learning models, and why you would want…

57 min
Protecting the Wild
Conservation Genomics between Taxonomy, Big Data,…

59 min
Provable Security
How I learned to stop worrying and love the backdoor

61 min
"The" Social Credit System
Why It's Both Better and Worse Than We can Imagine
58 min