Search for "olf" returned 7379 results

56 min
Household, Totalitarianism and Cyberspace
Philosophical Perspectives on Privacy Drawing on the…
61 min
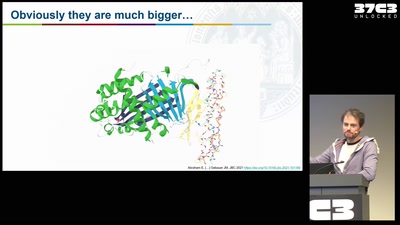
AlphaFold – how machine learning changed structural biology forever (or not?)
Getting first-hand insights into the impact of machine…
55 min
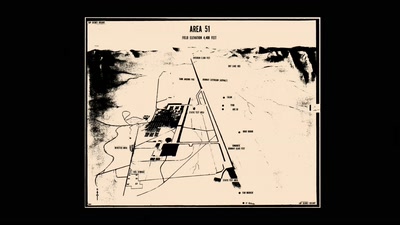
YOU’VE JUST BEEN FUCKED BY PSYOPS
UFOS, MAGIC, MIND CONTROL, ELECTRONIC WARFARE, AI, AND THE…
38 min
T-Minus Zero
The first days in the life of the "Flying Laptop" satellite

51 min
Anonymous, secure and easy. You can have them all.
An authentication protocol that offers security, privacy…
37 min
Code BROWN in the Air
A systemic update of sensitive information that you sniff…
31 min
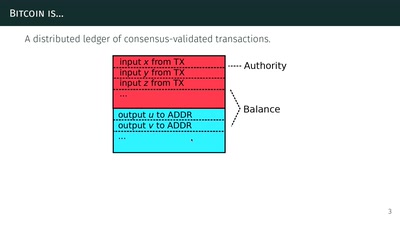
The Zcash anonymous cryptocurrency
or zero-knowledge succinct non-interactive arguments of…
55 min
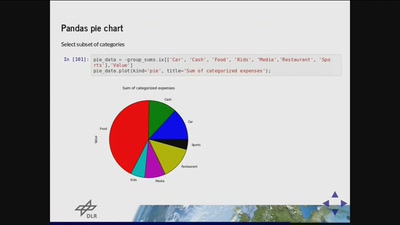
Data Analysis and Visualization with Python
Usage of Numpy, Pandas and Matplotlib for a personal…

60 min
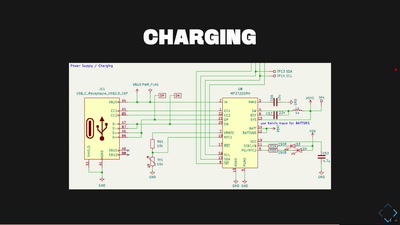
Low Cost High Speed Photography
Using microcontrollers to capture the blink of an eye for…
34 min
FeTAp 611 unplugged
Taking a rotary dial phone to the mobile age

57 min
TrustZone-M(eh): Breaking ARMv8-M's security
Hardware attacks on the latest generation of ARM Cortex-M…
41 min
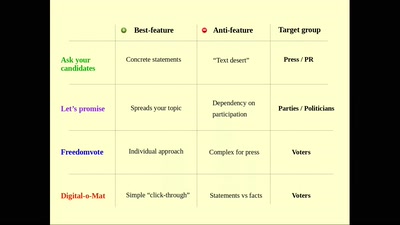
Ask your candidates and let everyone know about it
How to make use of democratic elections for your own purpose

36 min
Who's snitching my milk?
Nonlinear dynamics/analysis of vanishing bovine products in…

57 min
Software Reliability in Aerospace
An overview on design and generation of safe and reliable…
60 min
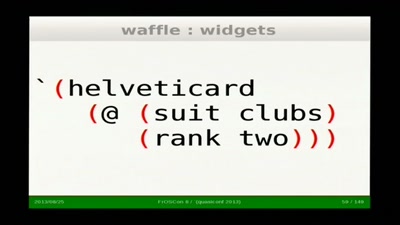
Building knodium.com with Scheme
First-hand experience report of a business application…
33 min
Computer Science in the DPRK
A view into technology on the other side of the world

43 min
#NoPNR – Let’s kill the next Data Retention Law
How to Stop the Dubious Use of Passenger Name Records by…
55 min
The good, the strange and the ugly in 2018 art &tech
On art, AI, hormones hacking and other prospects of a…

87 min
OPENCOIL – A Roaming Speedshow
or the fine art of appropriating inductive charging pads in…
52 min
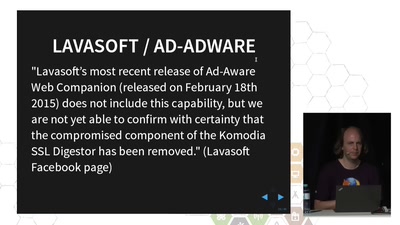
TLS interception considered harmful
How Man-in-the-Middle filtering solutions harm the security…
60 min
Lifting the Fog on Red Star OS
A deep dive into the surveillance features of North Korea's…

60 min
The Trust Situation
Why the idea of data protection slowly turns out to be…

48 min

